Complete Guide to DHCP Snooping, How it Works, Concepts, DHCP Snooping Database, DHCP Option 82, Mitigating DHCP Starvation Attacks, DHCP Hijacking, Man-in-the-Middle Attacks & Rogue DHCP Servers
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue DHCP servers and explains how security features like DHCP Snooping help protect networks from these attacks. We explain how DHCP Snooping works, cover DHCP Snooping terminology (trusted, untrusted ports/interfaces) and more. Finally we talk about the importance and purpose the DHCP Snooping Binding Database also used by Dynamic ARP Inspection to prevent ARP Poisoning and ARP Spoofing attacks.
Topics covered include:
- DHCP Starvation Attack, Man-in-the-Middle Attack, DHCP Hijacking & Reconnaissance Attacks
- Rogue DHCP Servers – A Major Security Threat & Source of Network Disruptions
- DHCP Snooping Support for Cisco Catalyst and Nexus Switches. Licensing & Features
- How DHCP Snooping Works – DHCP Snooping Concepts - Trusted, Untrusted Ports/Interfaces
- Traffic Dropped by DHCP Snooping, DHCP Snooping Violations – Syslog Messages
- The IP DHCP Snooping Binding Database – Dynamic ARP Inspection
- DHCP Snooping Option-82 Data Insertion
- Summary
Related Articles
- DHCP Option 82 Message Format, Analysis. DHCP Snooping Option 82 Injection & Removal Method, Trusted – Untrusted Switch Ports
- Basic & Advanced Catalyst Layer 3 Switch Configuration
- Understanding & Designing VLAN Networks
- Ethernet II Frame Formats
- MAC Address
DHCP Starvation Attack, Man-in-the-Middle Attack, DHCP Hijacking & Reconnaissance Attacks
DHCP Starvation attack is a common network attack that targets network DHCP servers. Its primary objective is to flood the organization’s DHCP server with DHCP REQUEST messages using spoofed source MAC addresses. The DHCP server will respond to all requests, not knowing this is a DHCP Starvation attack, and assign available IP addresses until its DHCP pool is depleted.
At this point the attacker has rendered the organization’s DHCP server useless and can now enable his own rogue DHCP server to serve network clients. DHCP Starvation is often accompanied by a Man-in-the-Middle attack as the rogue DHCP server distributes fake IP address parameters, including Gateway & DNS IP address, so that all client traffic passes through the attacker for inspection.
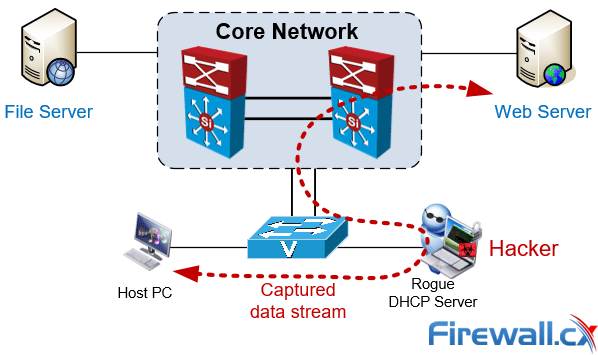 Typical Man-in-the-Middle attack. Client data streams flow through the attacker
Typical Man-in-the-Middle attack. Client data streams flow through the attacker
Using packet capture and protocol analysis tools the attacker is able to fully reconstruct any data stream captured and export files from it. In fact the process so simple it only requires a basic level of understanding of these type of network tools.
In other cases the Man-in-the-Middle attack can be used as a reconnaissance attack with the objective to obtain information about the network infrastructure, services but also identify hosts of high interest such as financial or database servers.
It should be by now evident how a simple attack can become a major security threat for any organization. The above attacks are examples on how easy hackers can infiltrate the network and get access to valuable information by simply connecting an unauthorized/untrusted device to an available network port effectively bypassing firewalls and other levels of security.
Rogue DHCP Servers – A Major Security Threat & Source of Network Disruptions
Rogue DHCP servers are a common problem within enterprise organizations and are not always directly related with an attack. Rogue DHCP Servers tend to appear out of nowhere thanks to users who connect consumer-grade network devices to the network infrastructure unaware that they have connected an unauthorized device with a rogue DHCP server enabled.
The Rogue DHCP server then begins assigning IP addresses to hosts within the network therefore causing network connectivity problems and in many cases – major service disruptions. In a best case scenario DHCP clients are served with an invalid IP address disconnecting them from the rest of the network. Worst case scenario would be the clients been assigned an IP address used by network infrastructure devices e.g the VLAN interface on the Core switch or a firewall interface, causing serious network disruptions and conflicts.
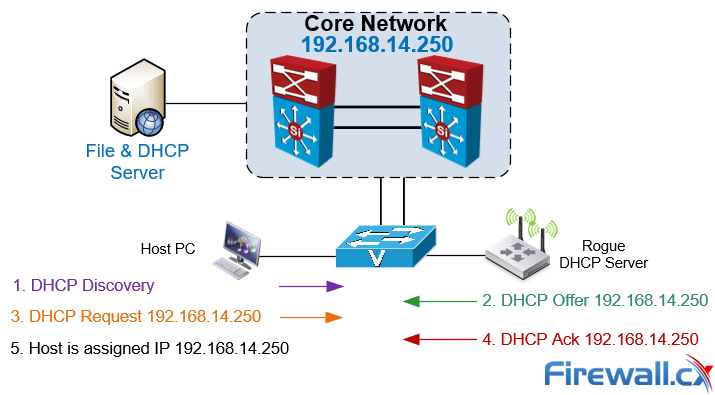
While many organizations enforce security policies that do not allow 3rd party or unauthorized devices to be connected to their network, there are still incidents where users who do not understand (or care about) the security implications continue to connect these devices to the network infrastructure without consulting their IT Department.
Educating users and enforcing security policies can be extremely challenging which is why security mechanisms need to be in place to help mitigate these incidents and is where DHCP Snooping comes into the picture.
DHCP Snooping Support for Cisco Catalyst and Nexus Switches. Licensing & Features
DHCP Snooping is available on both the Cisco Catalyst and Cisco Nexus platform switches. Both platforms are classified as enterprise-grade switches and fully support all DHCP Snooping functions.
DHCP Snooping is considered a standard security feature and does not require any additional licensing for the older Catalyst IOS, newer Catalyst IOS XE and Nexus NS-OS operating systems, therefore the feature is available and readily configurable on all switches.
Examples of Cisco Catalyst switches that support DHCP Snooping are: Cisco Catalyst 2960S, 2960-X, 3560, 3750, 3750-X, 3850, 4500, 6500, 9300, 9400 and 9500 series.
Examples of Cisco Nexus switches that support DHCP Snooping are: Nexus 2000, 3000, 5000, 7000 and 9000 series.
DHCP Snooping can be enabled globally and on a per-VLAN basis. This means you can enable it for all VLANs (globally) or only for specific including VLAN ranges e.g VLANs 1-20 & VLANs 45-50.
How DHCP Snooping Works – DHCP Snooping Concepts – Trusted, Untrusted Ports/Interfaces
DHCP Snooping is a Layer 2 security switch feature which blocks unauthorized (rogue) DHCP servers from distributing IP addresses to DHCP clients. In fact Cisco was the first vendor to implement DHCP Snooping as a security feature in its network switches and other vendors have since then followed with similar features.
It is important to note that DHCP SNOOPING is an access layer protection service – it does not belong in the core network.
The way DHCP Snooping works is fairly straight forward. DHCP Snooping categorizes all switchports into two simple categories:
- Trusted Ports
- Untrusted Ports
A Trusted Port, also known as a Trusted Source or Trusted Interface, is a port or source whose DHCP server messages are trusted because it is under the organization’s administrative control. For example, the port to which your organization’s DHCP server connects to is considered a Trusted Port. This is also shown in the diagram below:
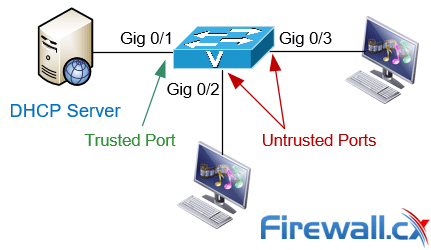
An Untrusted Port, also known as an Untrusted Source or Untrusted Interface, is a port from which DHCP server messages are not trusted. An example on an untrusted port is one where hosts or PCs connect to from which DHCP OFFER, DHCP ACK or DHCPNAK messages should never be seen as these are sent only by DHCP Servers.
Traffic Dropped by DHCP Snooping, DHCP Snooping Violations - Syslog Messages
When enabling DHCP Snooping the switch will begin to drop specific type of DHCP traffic in order to protect the network from rogue DHCP servers. Here is a list of the type of traffic DHCP Snooping will drop:
- DHCP Snooping will drop DHCP messages DHCPACK, DHCPNAK, DHCPOFFER originating from a DHCP server that is not trusted – that is, connected to an untrusted port.
- DHCP Snooping will drop DHCP messages that release or decline an offer if these messages are not originating from the port where the original DHCP conversation was held. This stops attackers from trying to terminate or decline a DHCP offer on behalf of the actual DHCP client.
- A DHCP relay agent forwards a DHCP packet that includes a relay-agent IP address that is not 0.0.0.0, or the relay agent forwards a packet that includes Option 82 information to an untrusted port. For an in-depth analysis please refer to our DHCP Option 82 article.
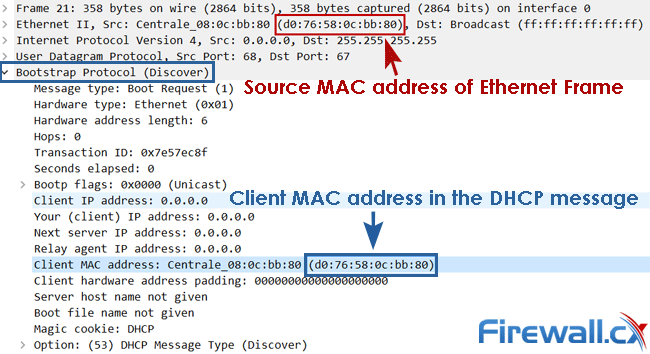
- DHCP Snooping will drop DHCP messages where the Source MAC address and client MAC address are not identical (see DHCP_SNOOPING-5-DHCP_SNOOPING_MATCH_MAC_FAIL below).
When DHCP Snooping detects a violation the DHCP packet(s) triggering the event is dropped and a message is logged in the switch’s log. The message can contain one of the following entries:
- %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP Snooping has detected DHCP server messages from an untrusted port. This is a serious violation and usually points to a rogue DHCP server operating on an untrusted port.
- %DHCP_SNOOPING-5-DHCP_SNOOPING_MATCH_MAC_FAIL: DHCP Snooping has detected the Source MAC address of the Ethernet frame and Client MAC address in the DHCP message are not identical (see image below).
The IP DHCP Snooping Binding Database – Dynamic ARP Inspection
When DHCP Snooping is enabled it will begin to build a dynamic database containing an entry for each untrusted host with a leased IP address if the host is associated with a VLAN that has DHCP Snooping enabled. No entries are created for hosts connected to trusted interfaces.
Each entry in the binding database contains the following information:
- MAC address of the untrusted host
- Leased IP address of the untrusted host
- Lease time
- Binding type
- VLAN number & interface the untrusted host is associated with
As untrusted hosts are assigned IP addresses from the trusted DHCP server the switch will automatically create new entries, update and cleanup the DHCP Snooping Binding Database.
For example, when an IP address lease expires or the switch receives a DHCPRELEASE message from the untrusted host, it will remove the specific entry from the database. On the other hand an entry will be created in the database if the switch sees a DHCPACK message from the trusted DHCP server acknowledging the assignment of an IP address to an untrusted host.
The show ip dhcp snooping binding command displays all entries inside the DHCP Snooping Binding Database:
Cat3560-Firewall.cx# show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------ ------------ ---------- ------------- ---- -----------------
D0:76:58:0C:BB:80 192.168.4.50 85228 dhcp-snooping 4 GigabitEthernet0/5
Total number of bindings: 1
The DHCP Snooping Binding Database is also used by other Layer2/3 security features such as Dynamic ARP Inspection which help protect the network against ARP Poisoning & ARP Spoofing attacks.
IP DHCP Snooping configuration for Cisco Catalyst and Cisco Nexus switching platforms will be covered extensively in an upcoming technical article.
Dynamic ARP Inspection, ARP Poisoning, ARP Spoofing attacks will be covered in an upcoming security article.
DHCP Snooping Option 82 – Relay Agent Information
The DHCP Option 82, aka Relay Agent Information Option, was originally created by RFC 3046 to allow the DHCP relay agent (e.g switch or router) to identify itself and the DHCP client that sent the DHCP messages. DHCP Option 82 is used in large metropolitan Ethernet-access deployments where DHCP is required to centrally manage the IP addresses for a large number of subscribers.
When DHCP Snooping is enabled on a Cisco Catalyst or Nexus switch, it will insert the Option 82 field field into the client’s DHCP message:
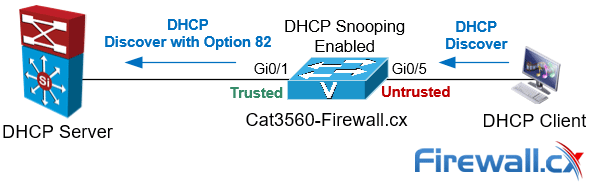
DHCP Option 82 is not often used within organizations but it does provide an additional layer of protection if the DHCP server supports it. For example the DHCP Server on Windows Server 2012 or 2016 supports Option 82 allowing administrators to create DHCP Policies that control the assignment of IP addresses to specific switches within the network.
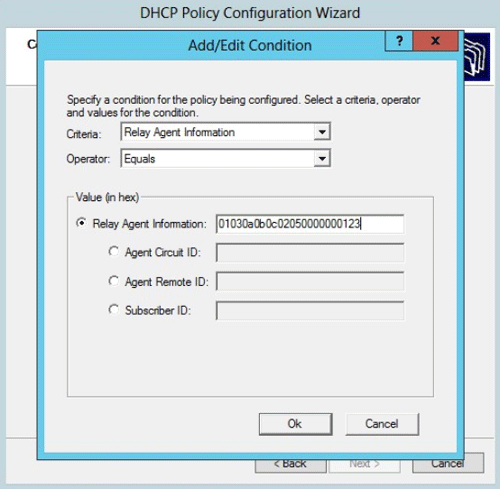
Analyzing the structure of DHCP Option 82 is out of this article’s scope but will be covered in great depth in an upcoming article.
Read our article "DHCP Option 82 Message Format, Analysis. DHCP Snooping Option 82 Injection & Removal Method, Trusted – Untrusted Switch Ports" for in-depth analysis of DHCP Option 82.
Summary
Man-in-the-Middle attacks and network disruptions from rogue DHCP servers is a serious network security threat organizations are faced to deal with on a daily basis. In this article we explained how Man-in-the-Middle attacks allow attackers to gain visibility of your network and can potentially lead exposing sensitive data flowing between servers and clients. We explained what DHCP Snooping is, examined how DHCP Snooping works and how it can effectively protect the network from these attacks. We looked at the type of traffic dropped by DHCP snooping, violation warnings and also explained the purpose and operation of the DHCP Snooping Binding Database. Finally we touched on the DHCP Snooping Option 82.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














