Suggested Articles:

ManageEngine Firewall Analyzer
Master Your Firewall: 6 Expert-Backed Steps to Bo…
In today’s evolving threat landscape, firewall audits are more than just a best practice—they're a critical line of defense. Regular audits ensure yo…
Network Protocol Analyzers
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Featured Subcategories:
WireShark Articles:
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
Popular Topics
Virtualization & VM Backup
Differences Between VMware vSphere, vCenter, ESXi Free…
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edition…
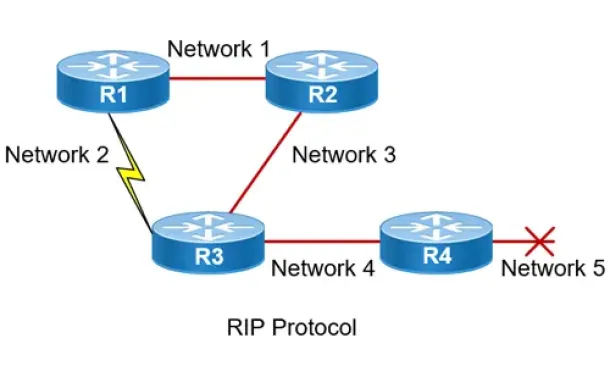
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
Network Protocol Analyzers
Advanced Network Protocol Analyzer Review: Colasoft Ca…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review, the…
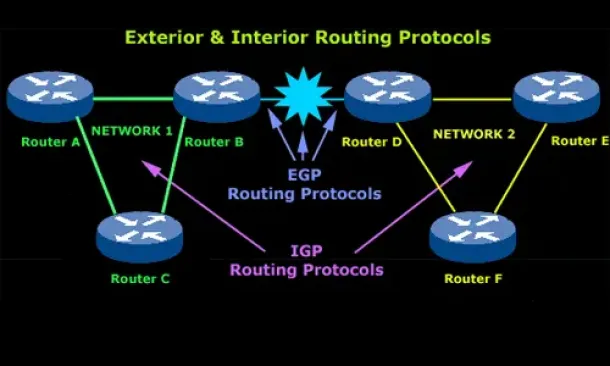
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
Cisco Routers
Enabling & Configuring SSH on Cisco Routers. Restrict…
This article shows how to configure and setup SSH for remote management of Cisco IOS Routers. We’ll show you how to check if SSH is supported by your IOS…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) Disp…
Cisco Configuration Professional (CCP) is Cisco’s latest GUI administration tool used to administer Cisco routers. CCP is basically the next step up from…
Cisco Routers
Configuring NAT Overload On A Cisco Router
NAT (Network Address Translation) is a method that allows the translation (modification) of IP addresses while packets/datagrams are traversing the networ…
Cisco Routers
Cisco GRE and IPSec - GRE over IPSec - Selecting and C…
GRE Tunnels are very common amongst VPN implementations thanks to their simplicity and ease of configuration. With broadcasting and multicasting support…



















