What is OWASP? Open Web Application Security Project - Helping Developers and Businesses Raise Awareness on Cyber-Security Attacks, Vulnerabilities and Security Threats
 With nearly every business sector relying on the internet and digital tools to function, it is no surprise that cybersecurity is the second-fastest growing industry. Hackers don’t care how large or small your company is. They will target all sizes in an all-out effort to steal data, access confidential or classified information, cause mayhem, and hurt the organization's reputation.
With nearly every business sector relying on the internet and digital tools to function, it is no surprise that cybersecurity is the second-fastest growing industry. Hackers don’t care how large or small your company is. They will target all sizes in an all-out effort to steal data, access confidential or classified information, cause mayhem, and hurt the organization's reputation.
Fortunately, not all hackers have nefarious intentions. The open source community is full with experts who are looking to warn people about threats and find the most effective ways to keep data safe. Many of those experts are a part of the Open Web Application Security Project (OWASP).
In this article, we'll cover the basics of OWASP and the critical role this work plays in the everyday operation of computers, servers, and other forms of modern technology. Topics covered include:
- What is OWASP? Introduction to Open Web Application Security Project
- Importance of Vendor Neutrality (OWASP)
- Why Web Application Security Matters
- The OWASP Top 10 List
- Accessing Digital Resources Securely
- Summary
What Is OWASP? Introduction To Open Web Application Security Project
OWASP was originally founded in 2001 by Mark Curphey and is run as a not-for-profit organization in the United States. The bulk of its contributors are pulled from the open-source community. Today, more than 32,000 people volunteer as part of OWASP's efforts, with much of their communication coming through message boards or email distribution lists.
The organization is designed to be an unbiased group focused on the best interests of the technology world as a whole. They will not promote specific vendor products or solutions. Instead, OWASP aims to provide practical information to organizations all across the world, with the goal of offering helpful security advice to bring about more informed decisions.
Where OWASP becomes particularly valuable is too small and medium-sized businesses that may not have a large IT budget and lack expertise when it comes to cybersecurity. Thanks to the documentation that OWASP creates, these types of organizations can gain a better understanding of where their systems are vulnerable and how to protect themselves better.
If you’ve heard of OWASP, it’s likely been in conjunction with a report they update every few years known as the OWASP Top 10. The list covers the most relevant cybersecurity threats facing the global community. Later in this article, we'll dive into some of the specifics referenced in the Top 10.
Importance of Vendor Neutrality (OWASP)
The OWASP community is firm about never endorsing specific products or services related to cybersecurity. This might seem counterintuitive. A company needs to make investments in certain tools if they hope to protect their digital assets. And knowing what vendors to trust is important.
However, the purpose of OWASP is to draw attention to the largest security threats we are facing today. If they were to accept advertising or payments for endorsements, then they would lose their impartial status and reliability. You would not know whether they were recommending a security tool because it was actually the best or because someone was paying them to say so.
In a perfect world, all security vendors would produce products and services that function as intended, whether they are developing virus scanners, malware detectors, or software firewalls. But the dirty underbelly of the industry is inhabited by the cybercriminals who try to disguise their attacks within security tools that are designed to look legitimate.
There is no perfect vulnerability security tool or solution, which is why OWASP avoids picking certain products to recommend. The members of OWASP want to highlight security risks to inspire organizations to go out and find a solution that works best for them.
Members of OWASP have a strict set of rules when it comes to dealing with vendors. There are not allowed to seek sales pitches or participate in a technology talk sponsored by a brand. No materials should be distributed in OWASP mailing lists that focus on particular vendors or products.
Why Web Application Security Matters
 Organizations with unimpressive IT budgets may be tempted to minimize how much they spend on security-related tools, activities, and training due to the challenge to mathematically determine what the return on investment (ROI) will be. If one thing is certain, it’s that management will want to know the ROI and when cyber-attacks are in play, coming up with an accurate representation of how much a successful penetration could have cost is, well, not easy.
Organizations with unimpressive IT budgets may be tempted to minimize how much they spend on security-related tools, activities, and training due to the challenge to mathematically determine what the return on investment (ROI) will be. If one thing is certain, it’s that management will want to know the ROI and when cyber-attacks are in play, coming up with an accurate representation of how much a successful penetration could have cost is, well, not easy.
But lowering the priority of cybersecurity protection is dangerous. Instead, you need to treat it like you would car insurance or health insurance. Everyone likes to think that they won't get into a car accident or have to go to the hospital, but insurance is there to cover you for unexpected incidents.
With IT security tools, you typically purchase a solution entirely or else pay for a subscription on a monthly basis. In either case, you spend money up front to avoid disaster for your entire organization. The point is to protect yourself from attacks before you even know you are being targeted.
Cybercriminals obsessively spend their lives looking for system vulnerabilities that can expose data or bring down entire servers. Usually, money is the primary objective, with the attackers seeking to sell stolen data on the dark web for profit. In some cases though, the attack is meant purely to destroy a company's reputation or ability to operate.
The goal of OWASP is to track the most common tactics that hackers utilize and identify what sort of protection is required to defend against them. New vulnerabilities are discovered every day, so that's why it's critical to maintain cybersecurity as an active part of your organization's operations. Buying a set of security tools is not enough. You need to keep those up to date and watch for new types of attacks that demand new types of solutions.
The OWASP Top 10 List
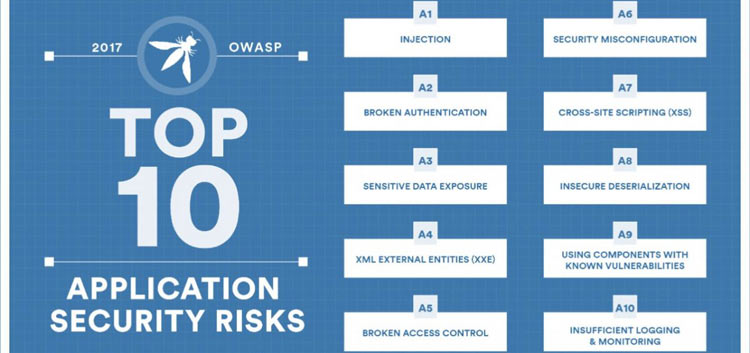
OWASP Top 10 List
As mentioned before, OWASP is best known for the Top 10 List of security vulnerabilities that they revise and publish regularly. The latest version is from 2017 and remains applicable today. The Top 10 List documentation includes an explanation of each risk as well as diagrams and prevention tips.
SQL Injection Attacks
Many of the threats on the Top 10 List are targeted at software developers who write code and may discover these types of security flaws during the course of their work. For example, the first risk listed is concerns database injections for SQL and other platforms. Hackers have used injection vulnerabilities for years to manipulate front-end inputs like search fields to retrieve or edit data that should be inaccessible to them.
Cross-Site Scripting Attacks
Another major code-based risk is cross-site scripting (XSS) attacks, where a cybercriminal will find a way to execute JavaScript or HTML on a remote webpage. Often, they will redirect users to a rogue URL where they try to steal personal information or financial data.
Best of the Rest
Some of the other items on the Top 10 List exist at a lower level of coding. For example, there are software libraries and frameworks that have known vulnerabilities that hackers can exploit. If your organization uses software that requires such an asset, then you should consider it to be at risk until it is patched.
But even if your coding standards are strict and secure, there are still risks that exist at a system or network level. Sensitive data exposure is included in OWASP's Top 10 List, as major data breaches have become a regular occurrence among businesses of all sizes and within all industries.
Accessing Digital Resources Securely
Obviously, OWASP is a huge fan of impressing upon organizations the critical need for internal and external users to only access digital resources securely. There are a variety of ways to accomplish this, not limited to:
- Forget the old advice that an eight character password is good enough. Modern password managers allow you to create incomprehensibly complex codes that run to 12 or 16 characters or longer.
- Think before you click. As social engineering scams have moved online, every member of your company needs to be educated to be suspicious of every link because a nasty bit of malware could be hiding on the other end.
- Use a virtual private network (VPN) in conjunction with your regular ISP. The cost is modest and it allows you to apply military-grade encryption to your data flow every time you go online. Another VPN benefit is that you receive a new anonymous IP address that makes it difficult for a bad guy to determine exactly where you are.
- Back up - as in backup your network regularly. There’s a decent chance a hacker will eventually be successful. At that point, your best defense is to be able to roll back the network to a previous point in history before the malware got in.
- Multi-Factor Authentication (MFA). MFA is quickly becoming an industry standard requiring users to verify their identity using additional means other than their password. Usually, the second authentication is a One-Time-Password (OTP) or a Push notification-verification via an application installed on the users’ phone.
There are hundreds of other preventative measures to take to keep your system safe but these four will get you a long way down the road while you get up to speed on all the security education OWASP has to offer.
Summary
Before you jump to purchasing costly solutions from vendors to cover each scenario on the OWASP Top 10 list, remember that a huge part of cybersecurity is awareness and education. Members of your organization should attend training on a regular basis to understand what risks exist for them both as users and system owners.
Following the lead of the OWASP community can help your company maintain a strong reputation. If your cybersecurity efforts are working properly, they should be invisible to people inside and outside of your organizations. Problems begin when a hacker manages to compromise your systems, leaving your digital assets and customers at risk.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














