- Posts: 158
- Thank you received: 1
MINIMUM SECURE configuration (baseline) -ipsec vpn
10 years 9 months ago - 10 years 9 months ago #38642
by skylimit
"...you are never too old to learn" anon
MINIMUM SECURE configuration (baseline) -ipsec vpn was created by skylimit
Hi,
Anyone have a security baseline document/guide for internet firewalls either for Cisco or just internet facing firewalls in generals? I've done a bit of search I'm getting very old guides.
So, what is the minimum security configuration to have for an internet firewall? Any Cisco, NSA, etc document will be most appreciated.
thanks
Anyone have a security baseline document/guide for internet firewalls either for Cisco or just internet facing firewalls in generals? I've done a bit of search I'm getting very old guides.
So, what is the minimum security configuration to have for an internet firewall? Any Cisco, NSA, etc document will be most appreciated.
thanks
"...you are never too old to learn" anon
Last edit: 10 years 9 months ago by skylimit.
10 years 9 months ago #38644
by skylimit
"...you are never too old to learn" anon
Replied by skylimit on topic Firewall baseline configuration
Since I didn't get any response to my question, I decided to change it a bit.
With regards IPsec VPN, what would be considered a "minimum" secure configuration? See IPsec VPN configuration below. In other words, what are the least/minimum settings that could be enabled while still having a secure IPsec VPN configuration? The idea is that I'm looking to compare "any" IPsec VPN configuration against the minimum requirement (i.e. baseline) so that I can tell if it's secure or not (compliant or not). I don't know if my question makes sense.
IPsec VPN configuration
Recall that an IPsec VPN router is exposed to the internet so it's security is important.
thanks
With regards IPsec VPN, what would be considered a "minimum" secure configuration? See IPsec VPN configuration below. In other words, what are the least/minimum settings that could be enabled while still having a secure IPsec VPN configuration? The idea is that I'm looking to compare "any" IPsec VPN configuration against the minimum requirement (i.e. baseline) so that I can tell if it's secure or not (compliant or not). I don't know if my question makes sense.
IPsec VPN configuration
Recall that an IPsec VPN router is exposed to the internet so it's security is important.
thanks
"...you are never too old to learn" anon
10 years 9 months ago #38645
by Chris
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Replied by Chris on topic Firewall baseline configuration
Skylimit,
Your question is an extremely good one and surely there is no one 'right' answer for it. It all depends on what the requirements are and what the firewall needs to secure behind it. For example, banks and financial departments have a much more 'strict' minimum configuration requirement, while companies are usually less strict and in most cases there is no guideline
In general there are a few 'best practices' which I follow and seem to have served me well so far. I'll include a few below but also make some remarks regarding VPN:
Regarding VPNs well there are things I always make sure of:
1) Always ensure your IPSec tunnel is properly encrypted using AES encryption
2) Never reveal your ISAKMP keys used for negotiation between tunnel ends (two routers)
3) Always ensure a different ISAKMP key is used for each tunnel endpoint
4) Ensure the necessary access lists are applied on both end of the tunnels, so that only the necessary traffic is to pass over the VPN
5) Use complex usernames/passwords or group passwords
6) Disable telnet/SSH access to the router from the public interface
7) Backup your configuration!!
 Never give others access to your router firewall!
Never give others access to your router firewall!
The above are just a few things I could write at 2am in the morning - I hope they help.
Chris,
Your question is an extremely good one and surely there is no one 'right' answer for it. It all depends on what the requirements are and what the firewall needs to secure behind it. For example, banks and financial departments have a much more 'strict' minimum configuration requirement, while companies are usually less strict and in most cases there is no guideline
In general there are a few 'best practices' which I follow and seem to have served me well so far. I'll include a few below but also make some remarks regarding VPN:
- Restrict remote access to the Firewall from the Outside (Public) and inside (Private) network
- Avoid Port Forwarding from the public interface directly to internal hosts on the local LAN
- Try not to configure Public IP addresses directly on the Firewall. In most cases, the router in front of the Firewall appliance is configured with Public IP addresses (WAN/LAN interfaces) and the LAN interface connects to the Firewall device. Instead of configuring these interfaces with Public IP, I always advise to forward any necessary public protocol (e.g TCP port 80 - www) from the router's WAN interface to the Firewall. Port-forwarding specific services and ports increase security dramatically
- Enable any stateful packet filtering (ASA 'Fixup' command) . Stateful Packet Filtering ensures all sessions are tracked and firewall access-lists are generated automatically to allow returning traffic through the firewall.
- Enable strong & complex user passwords
Regarding VPNs well there are things I always make sure of:
1) Always ensure your IPSec tunnel is properly encrypted using AES encryption
2) Never reveal your ISAKMP keys used for negotiation between tunnel ends (two routers)
3) Always ensure a different ISAKMP key is used for each tunnel endpoint
4) Ensure the necessary access lists are applied on both end of the tunnels, so that only the necessary traffic is to pass over the VPN
5) Use complex usernames/passwords or group passwords
6) Disable telnet/SSH access to the router from the public interface
7) Backup your configuration!!
The above are just a few things I could write at 2am in the morning - I hope they help.
Chris,
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
10 years 9 months ago - 10 years 9 months ago #38646
by skylimit
"...you are never too old to learn" anon
Replied by skylimit on topic Firewall baseline configuration
Thanks for the detailed answer, Chris.
These are really great. Are there any document/s from the likes of Cisco, the NSA, etc that list all you've mentioned please? This way I can justify them. So, it doesn't look like I just made them up. Of course, it it were for my home network for instance, I wont need any reference document.
I don't quite get what you mean here,
Thanks again.
Ps, I've actually done a bit of search for such baseline security configuration but can;t seem to find one document that lists them all.
These are really great. Are there any document/s from the likes of Cisco, the NSA, etc that list all you've mentioned please? This way I can justify them. So, it doesn't look like I just made them up. Of course, it it were for my home network for instance, I wont need any reference document.
I don't quite get what you mean here,
Also, why would you place a router in front of the firewall (exposing the router) instead of behind it. I don't have much experience with firewalls and their placement, so please pardon my question if it's obvious.Try not to configure Public IP addresses directly on the Firewall. In most cases, the router in front of the Firewall appliance is configured with Public IP addresses (WAN/LAN interfaces) and the LAN interface connects to the Firewall device. Instead of configuring these interfaces with Public IP, I always advise to forward any necessary public protocol (e.g TCP port 80 - www) from the router's WAN interface to the Firewall. Port-forwarding specific services and ports increase security dramatically
Thanks again.
Ps, I've actually done a bit of search for such baseline security configuration but can;t seem to find one document that lists them all.
"...you are never too old to learn" anon
Last edit: 10 years 9 months ago by skylimit. Reason: missing text
10 years 9 months ago - 10 years 9 months ago #38652
by Chris
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Replied by Chris on topic Firewall baseline configuration
SkyLimit,
You're mostly welcome.
Regarding the 'guide' your looking - I search and found exactly what you need.
Check out this Cisco URL which is basically part of the Enterprise Edge Design Guide. For your reference, 'best practices' for setups, configuration, services etc are called 'Design Guides' for Cisco. These are the key words for your search
www.cisco.com/c/en/us/td/docs/solutions/...G/SAFE_rg/chap6.html
The router is usually used to terminate the different WAN lines to the network, e.g ADSL, Ethernet WAN, Serial line and more. The other great thing about routers is that they are extremely flexible with multiple WAN connections as you can perform Policy-Based Routing (PBR) ( www.firewall.cx/cisco-technical-knowledg...a-auto-redirect.html ) and load-balance users between multiple connections, use IP SLA for automatic failover and much more...
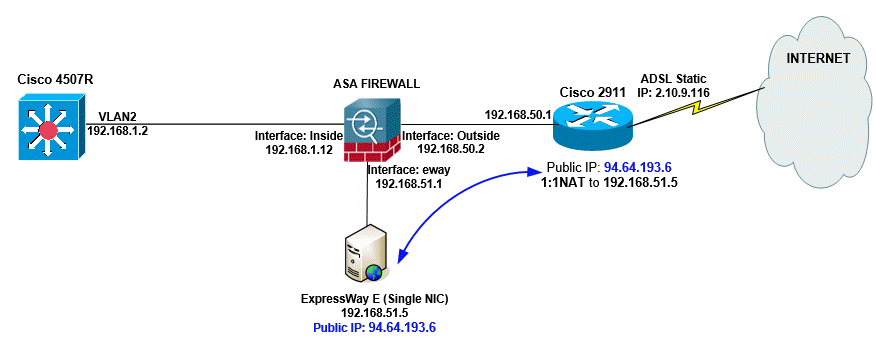
Finally, regarding the section that wasn't clear, what I meant is that when you have a Firewall and router in front, I usually configure the Firewall's WAN interface with a private IP (192.168.50.2), rather than a Public IP. This is shown in the diagram. I then use NAT to either create a one-to-one mapping with an internal host (ExpressWay-E Server) or simply port-forward only the ports required to the internal host (DMZ Zone always!!!).
Hope that helps clear things up. Let me know if you have any questions.
Chris.
You're mostly welcome.
Regarding the 'guide' your looking - I search and found exactly what you need.
Check out this Cisco URL which is basically part of the Enterprise Edge Design Guide. For your reference, 'best practices' for setups, configuration, services etc are called 'Design Guides' for Cisco. These are the key words for your search
www.cisco.com/c/en/us/td/docs/solutions/...G/SAFE_rg/chap6.html
The router is usually used to terminate the different WAN lines to the network, e.g ADSL, Ethernet WAN, Serial line and more. The other great thing about routers is that they are extremely flexible with multiple WAN connections as you can perform Policy-Based Routing (PBR) ( www.firewall.cx/cisco-technical-knowledg...a-auto-redirect.html ) and load-balance users between multiple connections, use IP SLA for automatic failover and much more...
Finally, regarding the section that wasn't clear, what I meant is that when you have a Firewall and router in front, I usually configure the Firewall's WAN interface with a private IP (192.168.50.2), rather than a Public IP. This is shown in the diagram. I then use NAT to either create a one-to-one mapping with an internal host (ExpressWay-E Server) or simply port-forward only the ports required to the internal host (DMZ Zone always!!!).
Hope that helps clear things up. Let me know if you have any questions.
Chris.
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Last edit: 10 years 9 months ago by Chris.
The following user(s) said Thank You: skylimit
10 years 9 months ago #38655
by skylimit
"...you are never too old to learn" anon
Replied by skylimit on topic Firewall baseline configuration
Hi Chris,
Thanks for your response again. Much appreciated.
In your IPsec configuration at the below link, if a 'crypto map' (and a crypto acl) is not configured on the outbound interface, is it possible that traffic will be sent unencrypted? Would this be something to look out for in order to ensure an ipsec vpn securely configured.
IPsec VPN configuration
Also, apart from the Phase 1 and Phase 2 parameters and possibly the crypto map, what other things should one check to ensure a secure configuration?
I thought I'd ask the question in this thread since it's related.
Thanks
Thanks for your response again. Much appreciated.
In your IPsec configuration at the below link, if a 'crypto map' (and a crypto acl) is not configured on the outbound interface, is it possible that traffic will be sent unencrypted? Would this be something to look out for in order to ensure an ipsec vpn securely configured.
IPsec VPN configuration
Also, apart from the Phase 1 and Phase 2 parameters and possibly the crypto map, what other things should one check to ensure a secure configuration?
I thought I'd ask the question in this thread since it's related.
Thanks
"...you are never too old to learn" anon
Time to create page: 0.119 seconds