Suggested Articles:

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…

ManageEngine Firewall Analyzer
7 Essential Firewall Management Strategies for Ma…
A firewall appliance is a fundamental pillar of network security, acting as the first line of defense against cyber threats. However, its strength…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…

EventLog Analyzer
Unlock Deep Visibility & Insight into Windows Ser…
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You'll also…
Featured Subcategories:
WireShark Articles:
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
How to Enable ‘Web Server’ Certificate Template Option…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server. …
Windows Servers
Simple Guide on Installing & Configuring a Windows 201…
A Windows Active Directory Certification Authority server (AD CA), also known as a Certificate Authority, is an essential service to every organization’s…
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. Analys…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual machine…
Windows Servers
How to Recover & Create "Show Desktop" Icon Function o…
The Show Desktop feature, included with almost all versions of Windows up to Windows 7, allows a user to minimize or restore all open programs and easily…
Popular Topics

Network Fundamentals
Introduction To Networking
A network is simply a group of two or more Personal Computers linked together. Many types of networks exist, but the most common types of networks are Loc…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
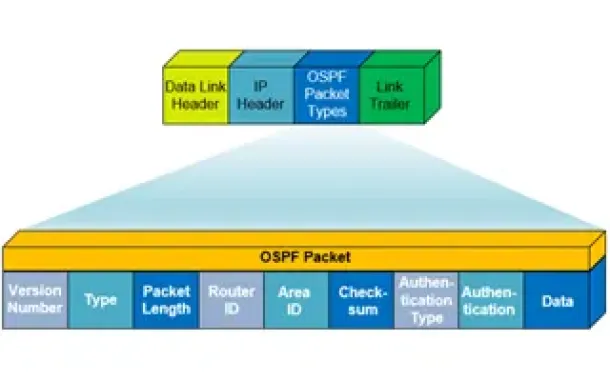
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
SASE & SD-WAN Networks
Converged SASE Backbone – How Leading SASE Provider, C…
Global connectivity is top of mind for many IT teams at organizations of all sizes. We are currently in the middle of a dramatic shift in business and tec…
Cisco Routers
Enabling & Configuring SSH on Cisco Routers. Restrict…
This article shows how to configure and setup SSH for remote management of Cisco IOS Routers. We’ll show you how to check if SSH is supported by your IOS…
Cisco Wireless
Introduction To Cisco Wireless Controllers (WLC) - Bas…
The Cisco Wireless Controller (WLC) series devices provide a single solution to configure, manage and support corporate wireless networks, regardless of t…

Cisco Data Center (Nexus/UCS)
Introduction to Cisco Nexus Switches – Nexus Product F…
This article introduces the Cisco Nexus product family (Nexus 9000, Nexus 7000, Nexus 5000, Nexus 3000, Nexus 2000, Nexus 1000V and MDS 9000). We explain…
Cisco Switches
Basic & Advanced Catalyst Layer 3 Switch Configuration…
This article covers basic and advanced configuration of Cisco Catalyst Layer-3 switches such as the Cisco Catalyst 3560G, 3560E, 3560-X, 3750, 3750E, 3750…



















