Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
ISDN Layers, Protocols & Components
| Read |
|
Articles:
Introduction To The ISDN Protocol
| Read |
|
Articles:
Introduction To Protocols
| Read |
|
Articles:
File Transfer Protocol - FTP
| Read |
|
Articles:
Trivial File Transport Protocol - TFTP
| Read |
|
Articles:
IPSec - Internet Protocol Security
| Read |
Suggested Articles:
ICMP Protocol
ICMP Protocol - Part 2: Echo / Echo Reply (Ping...
As mentioned in the previous page, an Echo is simply what we networking engineers call a 'ping'. The Echo Reply is, as most would guess, the ...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 5: TCP Window Siz...
Our fifth section contains some very interesting fields that are used by the TCP transport protocol. We see how TCP helps control how much data is ...
Network Cabling
10Base-T/2/5/F/35 - Ethernet
The 10Base-T UTP Ethernet and 10Base-2 Coax Ethernet were very popular in the early to mid 1990's when 100 Mbps network cards and hubs/switches wer...
Network Cabling
Straight Thru UTP Cables
This article covers the commonly known Unshielded Twisted Pair (UTP) cable and shows how many pairs the UTP Cat5, Cat5e, Cat6 & Cat7 cables con...
Featured Subcategories:
Netflow Articles:

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...

Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...

Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...

NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...
Your IP address:
18.221.53.209
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...
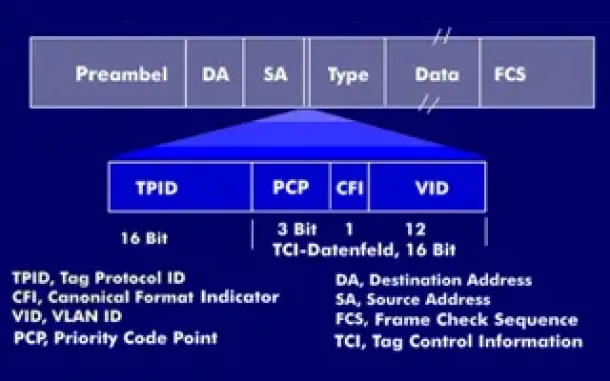
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently ...

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Sta...

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...
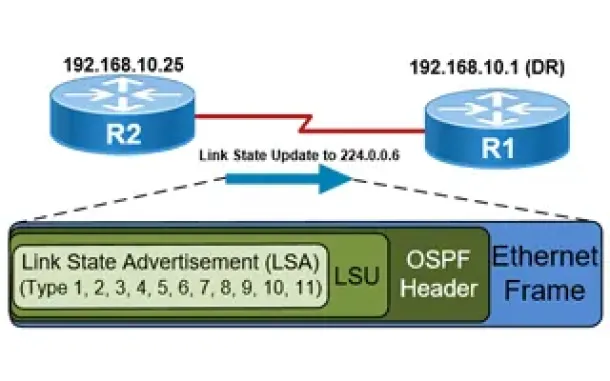
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (L...
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router rec...
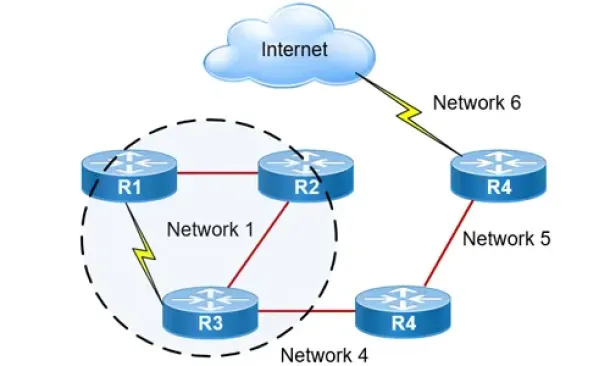
Routing
Hybrid Routing Protocols - Advantages and Disadvanta...
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scala...

Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other a...
Routing
Distance Vector Routing Protocols
Distance Vector routing protocols use frequent broadcasts (255.255.255.255 or FF:FF:FF:FF) of their entire routing table every 30 sec. on all their inte...
Network Protocol Analyzers
How to Use Multi-Segment Analysis to Troubleshoot Ne...
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubleshoot ...
Cisco Routers
How To Configure DHCP Server On A Cisco Router
DHCP (Dynamic Host Configuration Protocol) is the protocol used by network devices (such as PCs, network printers, etc) to automatically obtain correct ...
SASE & SD-WAN Networks
Key Features of a True Cloud-Native SASE Service. Se...
Secure Access Service Edge (SASE) is an architecture widely regarded as the future of enterprise networking and security. In previous articles we talked...
Cisco Routers
Installing Security Device Manager (SDM) on a Cisco ...
For years now, Cisco has been developing its Security Device Manager (SDM) software. This web-based software is designed to help the less experienced us...




















