Ensuring Compliance and Business Continuity in a Hybrid Work Environment
 In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office, or anywhere with a stable internet connection. Labeled as hybrid work, organizations have gradually started to adopt this seamless blend between remote work and on-site engagement.
In the wake of digital transformation, the work landscape as we know it has undergone a dynamic shift. People can now work from home, from the office, or anywhere with a stable internet connection. Labeled as hybrid work, organizations have gradually started to adopt this seamless blend between remote work and on-site engagement.
According to the digital readiness survey by ManageEngine, remote work will have a lasting impact with 96% of organizations stating that they will be supporting remote workers for at the least the next two years. While the remote working model offers significant advantages to employees, such as a better work-life balance, it presents significant challenges for organizations in extending office-like network security.
To ensure the success of hybrid work, every organization should address challenges related to security, compliance, and data protection. This article delves into the risks and issues associated with ensuring compliance in a hybrid work environment. Let's dive in.
Key Topics:
Network Compliance in a Hybrid Work Environment
Compliance refers to the adherence of an organization's infrastructure, configuration, and policies to industry standards. In a hybrid work environment where employees are working away from the office, it becomes difficult to ensure compliance. To overcome this, companies are employing a deluge of smart monitoring systems to make sure they stay compliant with industry norms.
Besides legal obligation, compliance also helps in safeguarding networks from security incidents such as breach attempts, overlooked vulnerabilities, and other operational inefficiencies.
Consequences of Compliance Violations
Non-compliance, which refers to the failure to adhere to laws, regulations, or established guidelines, can have a wide range of repercussions that vary depending on several factors. The severity of these consequences is often determined by the nature and extent of the violation, the specific mandate or regulation that has been breached, and the subsequent impact on various stakeholders involved. Here, we delve into the potential consequences of non-compliance in more detail:
- Substantial Fines: One of the most common consequences of non-compliance is the imposition of significant financial penalties. Regulatory bodies and government agencies often have the authority to levy fines on organizations or individuals found to be in violation of specific laws or regulations. These fines can be substantial and may escalate if the non-compliance persists or if there is evidence of willful negligence.
- Potential Lawsuits: Non-compliance can expose organizations to legal action from affected parties. Individuals, customers, or other businesses may choose to file lawsuits against non-compliant entities to seek compensation for damages or losses incurred as a result of the violation. Legal battles can be costly and time-consuming, further exacerbating the negative impact of non-compliance.
- Reputational Damage: Non-compliance can tarnish an organization's reputation, which can be challenging to rebuild. News of regulatory violations or unethical behavior can spread quickly through social media and news outlets, eroding trust and credibility in the eyes of customers, partners, and investors. Reputational damage can lead to reduced business opportunities, decreased customer loyalty, and difficulties in attracting top talent.
- Loss of Licenses or Accreditation: Many industries and professions require licenses or accreditation to operate legally. Non-compliance can result in the suspension or revocation of these licenses, effectively shutting down an organization's operations. For example, a healthcare facility found to be in violation of patient privacy regulations may lose its license to practice, rendering it unable to provide medical services.
- Operational Disruptions: Remedying non-compliance often necessitates operational changes and investments in compliance measures. This can disrupt day-to-day business operations and lead to increased costs. For instance, an organization might need to overhaul its data security protocols and systems in response to a data breach, incurring both financial and operational burdens.
- Loss of Market Share: As consumers become more informed and concerned about ethical business practices and compliance with regulations, non-compliance can lead to a loss of market share. Competitors who are seen as more trustworthy and compliant with legal requirements may gain a competitive advantage, further impacting the non-compliant organization's bottom line.
- Criminal Charges: In cases of severe non-compliance, especially those involving fraud, environmental violations, or other criminal activities, individuals within an organization may face criminal charges. This can result in fines, imprisonment, or both, and can have long-lasting personal and professional consequences.
Challenges in Upholding Compliance in a Hybrid Work Environment
Following are some of the significant challenges a network security admin will face while ensuring their organization stays compliant in a hybrid work environment:
Data and cybersecurity: Most security mandates demand that organizations operate within a secure networking framework. To ensure this, security admins implement the necessary security practices, including data encryption, access restriction, and securing remote connections.
Auditing: Meeting security mandates requires organizations to implement access control, track data changes, and monitor data movement within the organization. Remote work complicates the process of achieving visibility in this regard, demanding the use of sophisticated tools for monitoring and documenting these modifications.
Device and network security: Hybrid work has introduced a multitude of devices into the corporate environment. Compliance standards require endpoint devices to stay protected and regularly updated, and adhere to security norms to make sure network security stays uncompromised.
Secure collaboration and communication: Communication tools serve as the lifeline of remote work, and compliance standards extend to these solutions as well. Compliance mandates dictate organizations to analyze, track, and secure communication data.
By employing specialized compliance management tools, a significant portion of the troubles faced by organizations in ensuring network compliance can be negated.
Mitigating the Challenges with ManageEngine
ManageEngine's ITOM suite contains various solutions boasting AI capabilities designed to simplify and cater to all your network monitoring needs. Among these, the combination of ManageEngine Firewall Analyzer and ManageEngine Network Configuration Manager equips you to tackle the complexities of compliance in a hybrid work environment effectively.
The duo offers a robust framework for data security and enforcing traffic and configuration management. With the help of these tools, organizations can effortlessly manage compliance, protect sensitive data, and commit to data protection and privacy.
Firewall Analyzer
ManageEngine Firewall Analyzer is a multi-vendor, agentless, comprehensive network security and device management solution. It helps optimize firewall performance, manage VPNs, comply with mandates, generate log-based reports, assist with security audits, and more.
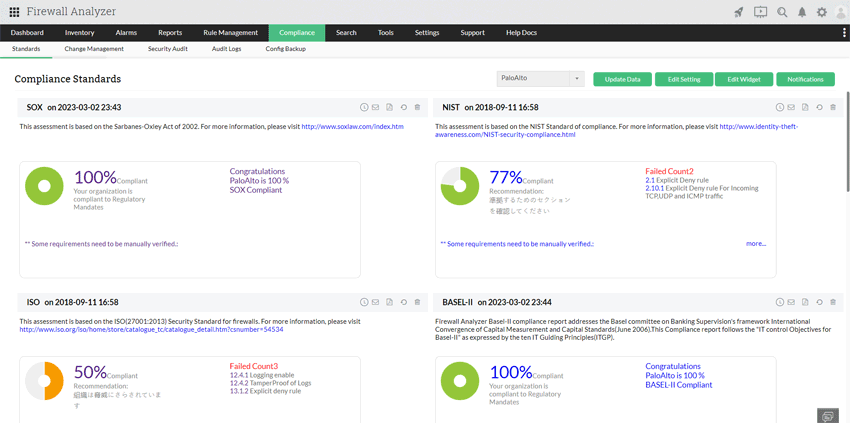 ManageEngine Firewall Analyzer (click to enlarge)
ManageEngine Firewall Analyzer (click to enlarge)
1. Traffic monitoring: Monitor network traffic in real time, spot abnormalities in traffic activity, and identify potential threats to the network.
2. Compliance reports: Generate reports right out of the box for around 10 network security compliance mandates to meet compliance benchmarks.
3. Security audits: Conduct security audits to identify vulnerabilities, compliance gaps, outdated firewall rules, and potential security threats.
4. Log retention: Configure log data retention in the database according to the time period required by each compliance mandate.
Network Configuration Manager
ManageEngine Network Configuration Manager is a robust configuration management solution designed to simplify and automate device configurations. It also helps you identify misconfigurations, perform firmware updates, check compliance, make configuration backups, and more.
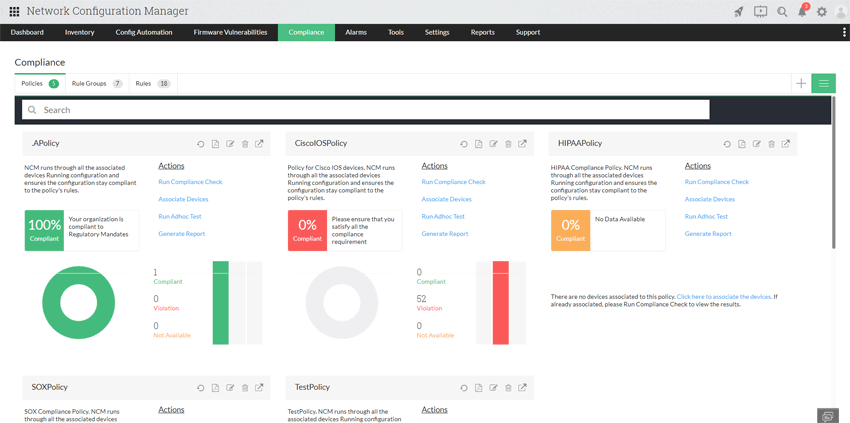 ManageEngine Network Configuration Manager (click to enlarge)
ManageEngine Network Configuration Manager (click to enlarge)
1. Configuration backups: Automate configuration backups for quick recovery in the event of a security breach or if there is an issue with the latest configuration.
2. Change management: Track the who, when, and what of the configuration changes made to your device configurations, and prevent unauthorized changes from being made.
3. Compliance policies: Create custom policies based on local or internal requirements, and deploy quick fixes to regulate compliance violations.
4. Compliance audits: Conduct mock audits to check preparedness, and perform regular, periodic audits to ensure the network stays compliant with relevant mandates.
Summary
Embrace the power of ManageEngine's tools to pave a compliant and secure path in the hybrid work landscape. Network Configuration Manager and Firewall Analyzer are part of the ManageEngine ITOM suite of solutions that offers network monitoring, sever monitoring, application monitoring, bandwidth monitoring, and IP address and switch port management in addition to compliance management. Try a free 30-day trial today.
Your IP address:
3.143.218.146
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!


















