- Posts: 5
- Thank you received: 0
How to subnet and add VLANS into my network
11 years 10 months ago #38482
by AdminOmid
How to subnet and add VLANS into my network was created by AdminOmid
Hello -First let me say I have posted this on cisco support forums and just copied and pasted into a new question for you here. Secondly I think I understand that to route through subnets I need a router between each subnet with a unique IP address for each subnet on each router. please correct me if I'm wrong. Thirdly I think I understand that I need a router to communicate between vlans on different subnets. Please correct me if I'm wrong. And thirdly to communicate between vlans on the same subnet all I need is a layer 2 switch between vlans. Please correct me if I'm wrong.
Now here's my post to cisco community from today that I just copied and pasted here. Please help out with any corrections, ideas, and comments on how to do what I want to do. I hope I have the whole concept down.
I have a scenario that I'm hoping I can get some help with. I'll be as detailed and descriptive as I can.
This is for a business with 100 employees nodes and 100 camera nodes all needing IP internet through private addressing and public gateway.
I have a business class gateway with a private range of 12 public addresses. their modem does nothing but act as a gateway since I have disabled the firewall and DHCP.
In place of the firewall and DCHP from the modem i have installed a RV120 Firewall with VPN. When installing I replicated the IP scheme of the modem as to not disturb and disrupt the devices assigned addresses from that scheme from the modem. I did this because the owner could not have any down time or any disruption to the business operations.
The RV120 now acts as firewall , DHCP , and VPN. I'll address the subnet first. I's using 10.0.0.0/24 subnet range.
DHCP is assigning 10.1.10.50 - 10.1.10.100 the rest are static and i plan to use static DHCP with the IP and MAC assigned to each static DHCP address.
There are 100 cameras with static IP addresses in the range of 10.1.10.11 - 10.1.10.40, and 10.1.0.1.101 - 10.1.10.170.
VPN uses PPTP assigned address 10.1.10.6 - 10.1.10.10.
There are no layer 3 switches that i know of. Just a layer two that is the primary switch and ports have run out, and various out of the box switches and wireless access points connected to the primary switch.
I want to implement subnets into the network and VLANS as well on a new Layer 3 switch from cisco. Thinking 3550 from Cisco or one of the older layer 2 switches with layer three capabilities.
Any comments at all, idea, knowledge not matter how trivial please help by responding. My network diagram with these ideas will follow.
Thanks
Now here's my post to cisco community from today that I just copied and pasted here. Please help out with any corrections, ideas, and comments on how to do what I want to do. I hope I have the whole concept down.
I have a scenario that I'm hoping I can get some help with. I'll be as detailed and descriptive as I can.
This is for a business with 100 employees nodes and 100 camera nodes all needing IP internet through private addressing and public gateway.
I have a business class gateway with a private range of 12 public addresses. their modem does nothing but act as a gateway since I have disabled the firewall and DHCP.
In place of the firewall and DCHP from the modem i have installed a RV120 Firewall with VPN. When installing I replicated the IP scheme of the modem as to not disturb and disrupt the devices assigned addresses from that scheme from the modem. I did this because the owner could not have any down time or any disruption to the business operations.
The RV120 now acts as firewall , DHCP , and VPN. I'll address the subnet first. I's using 10.0.0.0/24 subnet range.
DHCP is assigning 10.1.10.50 - 10.1.10.100 the rest are static and i plan to use static DHCP with the IP and MAC assigned to each static DHCP address.
There are 100 cameras with static IP addresses in the range of 10.1.10.11 - 10.1.10.40, and 10.1.0.1.101 - 10.1.10.170.
VPN uses PPTP assigned address 10.1.10.6 - 10.1.10.10.
There are no layer 3 switches that i know of. Just a layer two that is the primary switch and ports have run out, and various out of the box switches and wireless access points connected to the primary switch.
I want to implement subnets into the network and VLANS as well on a new Layer 3 switch from cisco. Thinking 3550 from Cisco or one of the older layer 2 switches with layer three capabilities.
Any comments at all, idea, knowledge not matter how trivial please help by responding. My network diagram with these ideas will follow.
Thanks
11 years 10 months ago #38483
by Chris
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Replied by Chris on topic How to subnet and add VLANS into my network
AdminOmid,
Thanks for your post and welcome to Firewall.cx
Regading your first set of questions about VLANs and routing between them, we've got a whole section dedicated to VLAN networks and routing packets between them (InterVLAN Routing).
The following link covers VLANs:
www.firewall.cx/networking-topics/vlan-networks.html
And here you'll find specific information about InterVLAN Routing:
www.firewall.cx/networking-topics/vlan-n...tervlan-routing.html
In short, yes, you need a router to route between subnets. In case of VLANs, this can be achived either through a Layer-3 Switch (3550 as you mentioned) or using a physical Cisco router configured for "Router-on-a-Stick' ( www.firewall.cx/cisco-technical-knowledg...1q-router-stick.html ).
Coming to your scenario with you Cameras and the RV120, it would certainly help if you could provide a diagram, however I found one issue which I'm not sure if I understood it correctly. You said that you enabled DHCP on the RV120 using the 10.0.0.0/24 range, hwever then you say that the DHCP is assigning 10.1.10.X - which is a completely different subnet from 10.0.0.0/24 - How is this possible?
If you can post a brief diagram and explain as simple as possible what you want to do, we'll surely be able to help you with it.
Thanks.
Chris.
Thanks for your post and welcome to Firewall.cx
Regading your first set of questions about VLANs and routing between them, we've got a whole section dedicated to VLAN networks and routing packets between them (InterVLAN Routing).
The following link covers VLANs:
www.firewall.cx/networking-topics/vlan-networks.html
And here you'll find specific information about InterVLAN Routing:
www.firewall.cx/networking-topics/vlan-n...tervlan-routing.html
In short, yes, you need a router to route between subnets. In case of VLANs, this can be achived either through a Layer-3 Switch (3550 as you mentioned) or using a physical Cisco router configured for "Router-on-a-Stick' ( www.firewall.cx/cisco-technical-knowledg...1q-router-stick.html ).
Coming to your scenario with you Cameras and the RV120, it would certainly help if you could provide a diagram, however I found one issue which I'm not sure if I understood it correctly. You said that you enabled DHCP on the RV120 using the 10.0.0.0/24 range, hwever then you say that the DHCP is assigning 10.1.10.X - which is a completely different subnet from 10.0.0.0/24 - How is this possible?
If you can post a brief diagram and explain as simple as possible what you want to do, we'll surely be able to help you with it.
Thanks.
Chris.
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
11 years 10 months ago #38484
by AdminOmid
Replied by AdminOmid on topic How to subnet and add VLANS into my network
Hey Chris.
Appreciate it.
I think the right range would be 10.1.10.1/24
I incorrectly used 10.0.0.0/24 to identify the mask of 255.255.255.0 = 24.
Thanks for the correction. You were the first person to catch that. I think everyone else made the assumption that I was just referring the mask and ignoring the subnet as it were.
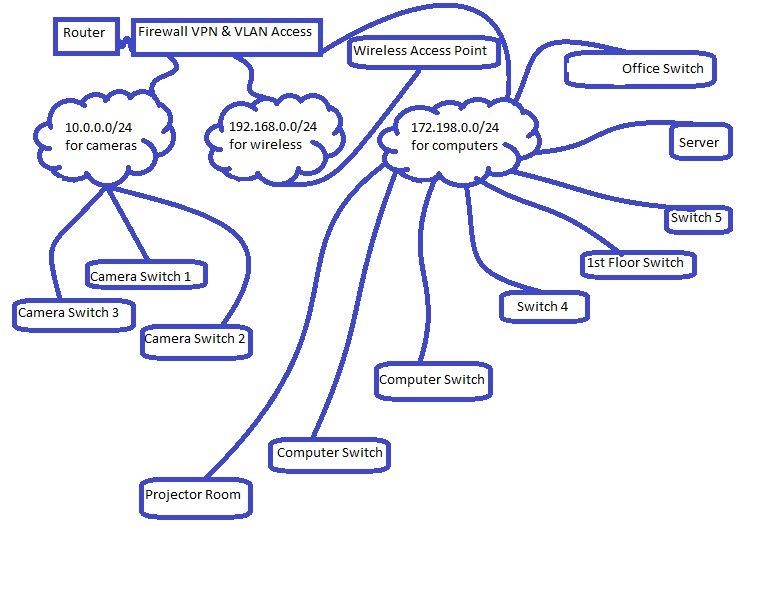
I have posted a quick diagram of what I want to do.
In short I want to replace out of the box Linksys switches with Layer 3 switches and attach them to VLAN subnets on my VPN firewall VLAN ports. Three different subnets.
See anything wrong with it?
Appreciate it.
I think the right range would be 10.1.10.1/24
I incorrectly used 10.0.0.0/24 to identify the mask of 255.255.255.0 = 24.
Thanks for the correction. You were the first person to catch that. I think everyone else made the assumption that I was just referring the mask and ignoring the subnet as it were.
I have posted a quick diagram of what I want to do.
In short I want to replace out of the box Linksys switches with Layer 3 switches and attach them to VLAN subnets on my VPN firewall VLAN ports. Three different subnets.
See anything wrong with it?
11 years 10 months ago - 11 years 10 months ago #38485
by Chris
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Replied by Chris on topic How to subnet and add VLANS into my network
AdminOmid,
The network you want to create is defiantely doable - I see no problem with it.
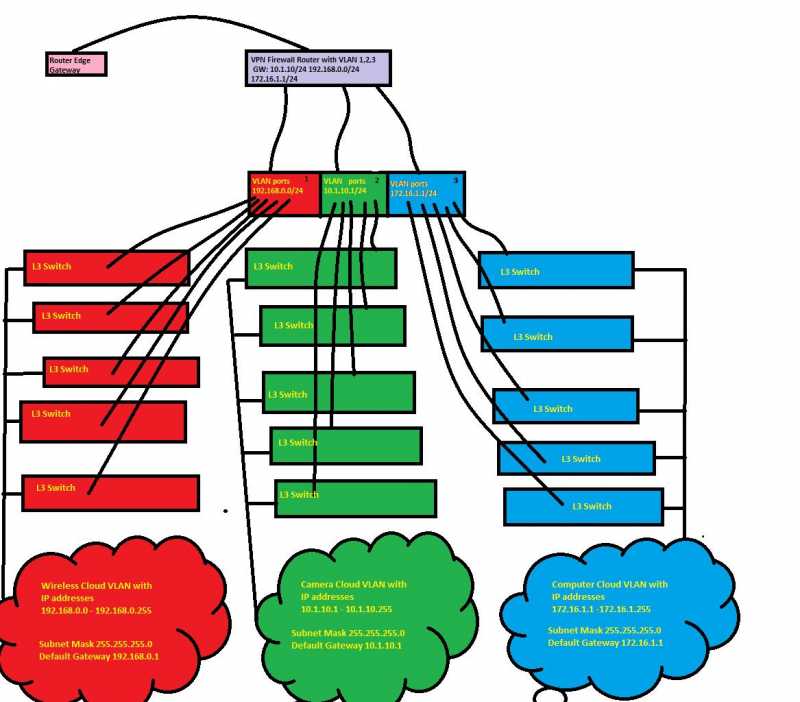
The way I see it, you can place a Layer-3 switch right behind the VPN Firewall and create another 3 VLANs, one for each of your networks (clouds). This way, you will only require one Layer-3 switch to interconnect all networks. The same Layer-3 switch will have the VPN-Firewall as its Gateway.
E.G:
The L3 switch will have a total of 4 VLANS:
VLAN1 - 192.168.1.0/24: Connects Firewall-VPN with L3 Switch
VLAN 2 - 10.0.0.0/24: Connects Camera VLAN
VLAN 3 - 192.168.0.0/24 : Wireless VLAN
VLAN 4 - 172.198.0.0/24: Computers VLAN
You'll also need in this scenario to add 3 static routes at your Firewall-VPN, in order to ensure it knows how to reach the 3 remote VLANS/Networks.
The other alternative would be to all 3 VLANs/networks directly to the Firewall-VPN. This would require the Firewall-VPN device to support multiple VLANs and have at least 3 LAN Ethernet Interfaces of which one will be assigned to each VLAN/Network.
Hope this helps!
The network you want to create is defiantely doable - I see no problem with it.
The way I see it, you can place a Layer-3 switch right behind the VPN Firewall and create another 3 VLANs, one for each of your networks (clouds). This way, you will only require one Layer-3 switch to interconnect all networks. The same Layer-3 switch will have the VPN-Firewall as its Gateway.
E.G:
Code:
Router< ----> VPN-Firewall(192.168.1.0/24) < -----> (192.168.1.0/24 VLAN1) Layer-3-Switch ---- 3 Uplinks,one to each cloud/network.
The L3 switch will have a total of 4 VLANS:
VLAN1 - 192.168.1.0/24: Connects Firewall-VPN with L3 Switch
VLAN 2 - 10.0.0.0/24: Connects Camera VLAN
VLAN 3 - 192.168.0.0/24 : Wireless VLAN
VLAN 4 - 172.198.0.0/24: Computers VLAN
You'll also need in this scenario to add 3 static routes at your Firewall-VPN, in order to ensure it knows how to reach the 3 remote VLANS/Networks.
The other alternative would be to all 3 VLANs/networks directly to the Firewall-VPN. This would require the Firewall-VPN device to support multiple VLANs and have at least 3 LAN Ethernet Interfaces of which one will be assigned to each VLAN/Network.
Hope this helps!
Chris Partsenidis.
Founder & Editor-in-Chief
www.Firewall.cx
Last edit: 11 years 10 months ago by Chris.
11 years 10 months ago - 11 years 10 months ago #38486
by AdminOmid
Replied by AdminOmid on topic How to subnet and add VLANS into my network
Thanks Chris - thanks again!. I do have one more thing I need clarification on. Reading through the intervlan routing link you provided I saw that there are trunk lines between the switches. That confused me. In my design I have one core switch (main distribution switch) that has many other switches attached to it through cat cabling. There are no trunk lines to speak of between the switches as they are all in the same physical building (rather large building) and spread out.
My plan if this makes sense was to enable the VLANS on the firewall , attach the main layer 3 switch and route traffic through the vlans assigning ports for each on the core switch for those other switches on the various vlans.
Does any of this make sense? Am I going about it right? If I had my lab setup I could test this all out but without purchasing the equipment first that's not possible. I don't want to purchase unnecessary switches or purchase the wrong hardware altogether.
one more thing. my firewall has 5 ports. 1 for WAN and 4 Ethernet ports. I'm assuming I can just use one port to one core switch and do the traffic routing through port VLAN assignments on the switch.. is that possible? I'm asking because it doesn't look like my firewall needs to use the Ethernet ports for the different VLANS as long as there are VLAN ID's all VLANS are accessible through a single Ethernet port, I think. Its not a problem if I have to assign/attach each port to a VLAN.
Hope I haven't confused you. This is all made more difficult being I am doing this all remotely and have no physical access to my site.
Thanks
AdminOmid
My plan if this makes sense was to enable the VLANS on the firewall , attach the main layer 3 switch and route traffic through the vlans assigning ports for each on the core switch for those other switches on the various vlans.
Does any of this make sense? Am I going about it right? If I had my lab setup I could test this all out but without purchasing the equipment first that's not possible. I don't want to purchase unnecessary switches or purchase the wrong hardware altogether.
one more thing. my firewall has 5 ports. 1 for WAN and 4 Ethernet ports. I'm assuming I can just use one port to one core switch and do the traffic routing through port VLAN assignments on the switch.. is that possible? I'm asking because it doesn't look like my firewall needs to use the Ethernet ports for the different VLANS as long as there are VLAN ID's all VLANS are accessible through a single Ethernet port, I think. Its not a problem if I have to assign/attach each port to a VLAN.
Hope I haven't confused you. This is all made more difficult being I am doing this all remotely and have no physical access to my site.
Thanks
AdminOmid
Last edit: 11 years 10 months ago by AdminOmid.
11 years 10 months ago - 11 years 10 months ago #38487
by AdminOmid
Replied by AdminOmid on topic How to subnet and add VLANS into my network
Last edit: 11 years 10 months ago by AdminOmid.
Time to create page: 0.158 seconds