Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
|
Articles:
VLAN Security - Making the Most of VLANs
| Read |
|
Articles:
VTP Pruning
| Read |
|
Articles:
VTP Protocol - In-Depth Analysis
| Read |
|
Articles:
VTP Introduction & Modes
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
VLANs - Access & Trunk Links
| Read |
|
Articles:
Dynamic VLANs
| Read |
|
Articles:
Static VLANs
| Read |
| Read | |
|
Articles:
The VLAN Concept - Introduction to VLANs
| Read |
Suggested Articles:

Network Fundamentals
Media Access Control - MAC Addresses
A MAC address, or Media Access Control address, is a unique identifier assigned to a network interface controller (NIC) for use as a network addres…
Network Address Translation - NAT
Network Address Translation (NAT) Concepts
Before we dive into the deep waters of NAT, we need to make sure we understand exactly what NAT does. So let me give you the background of NAT, why i…
Subnetting
IP Subnetting - Part 1: The Basic Concepts
When we subnet a network, we basically split it into smaller networks. For example, when a set of IP Addresses is given to a company, e.g 254 they mi…
Ethernet Protocol, CSMA/CD, Collisions
Late Ethernet Collisions
Late collisions, on the other hand, are not normal and are usually the result of out of spec. cabling or a malfunctioning adapter. A late collision i…
Featured Subcategories:
Netflow Articles:
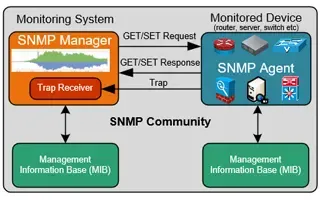
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
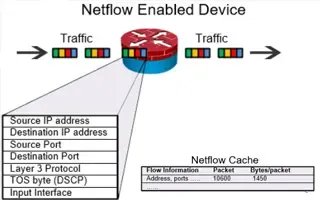
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
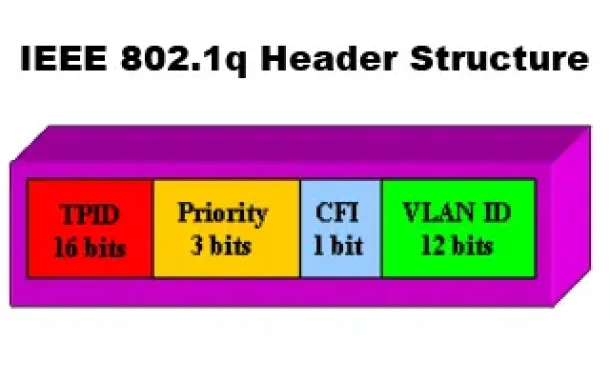
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
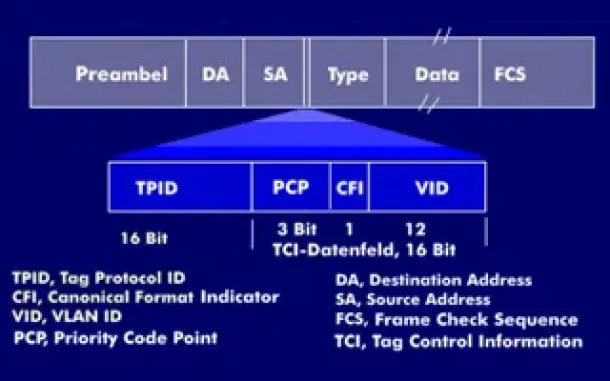
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
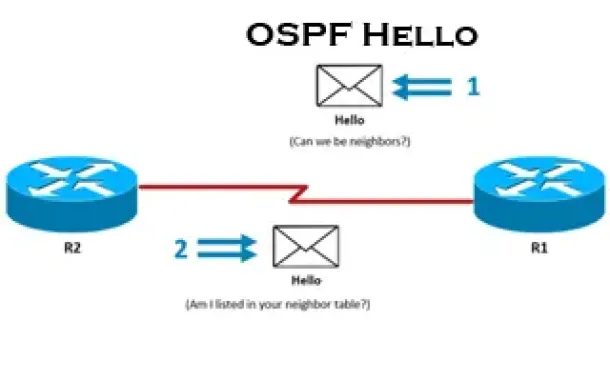
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
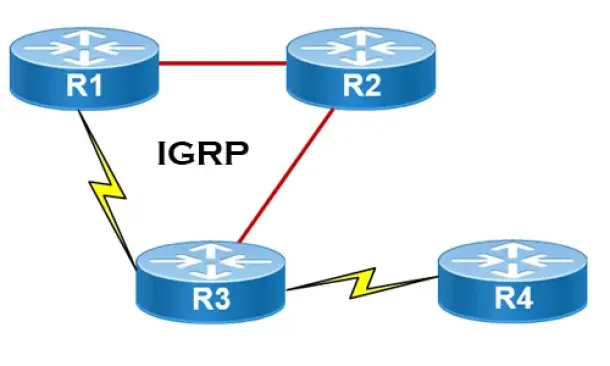
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
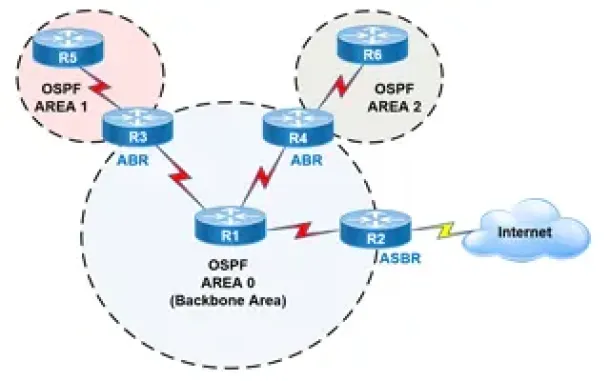
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
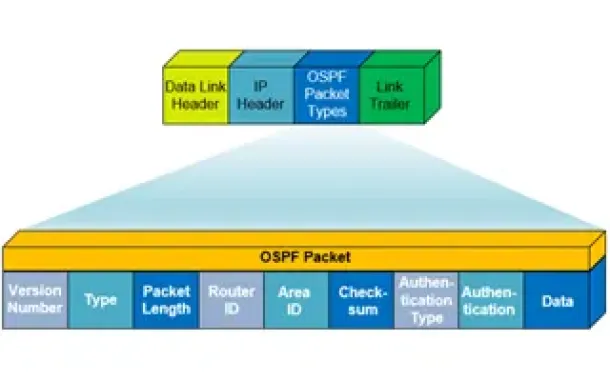
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Cisco Switches
Cisco Nexus 7000 Series Module Shutdown and Removal Pr…
This article explains the procedure that should be followed to correctly shutdown/powerdown a Cisco Nexus 7000 series module and remove it from the chassi…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) Disp…
Cisco Configuration Professional (CCP) is Cisco’s latest GUI administration tool used to administer Cisco routers. CCP is basically the next step up from…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…



















