Suggested Articles:
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobile…
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to pro…

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into OpM…
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberattac…
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Featured Subcategories:
WireShark Articles:
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…
Windows Servers
Windows Server 2012 File Server Resources Manager (FSR…
The Windows Server 2008 first carried FSRM or Fie Server Resources Manager, which allowed administrators to define the file types that users could save to…
Windows Servers
Installing Windows Server 2012 Active Directory via Se…
This article serves as an Active Directory tutorial covering installation and setup of a Windows 2012 Domain Controller using Windows Server Manager (GUI)…
Windows Servers
How to Install Windows Server 2012 from USB Flash – IS…
Most would remember the days we had to have a CDROM or DVDROM in order to proceed with the installation of an operating system. Today, it is very common i…
Windows Servers
Installing Active Directory Services & Domain Controll…
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controller…
Popular Topics
Routing
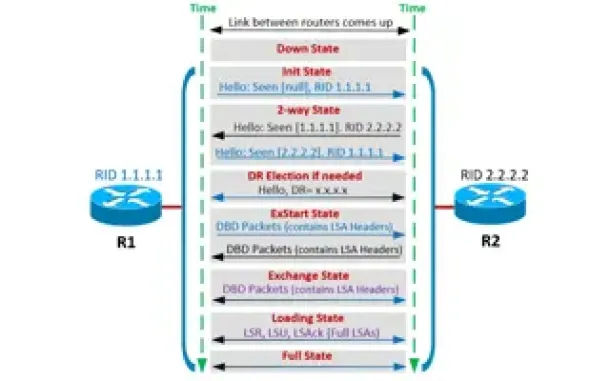
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
SASE & SD-WAN Networks
The Need for a Converged SASE Platform. Converging Net…
The digital transformation is pushing applications to the cloud, the 2020-2022 pandemic shifted employees to work from home, and the number of resulting n…
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Configu…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes the…
Windows Servers
Guide to Windows Server 2016 Hyper-V Hypervisor: New V…
One of Windows Server 2016 highlights is the newer Hyper-V server that not only extends the hypervisor’s features and capabilities but also introduces a n…
Cisco Routers
How To Fix Cisco Configuration Professional (CCP) Disp…
Cisco Configuration Professional (CCP) is Cisco’s latest GUI administration tool used to administer Cisco routers. CCP is basically the next step up from…
Cisco Wireless
Understanding, Configuring & Tweaking Web-based Cisco…
Cisco Aironet Access Points, just like most Cisco devices, provide a web interface from which we are able to configure the device. It is often we are pres…
Cisco Switches
Resolving Cisco Switch & Router ‘DHCP Server Pool Exha…
In previous articles, we showed how it is possible to configure a Cisco router or Catalyst switch to provide DHCP server services to network clients. Ever…
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & Fi…
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and d…



















