Suggested Articles:
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…

OpManager - Network Monitoring & Management
Elevate your network management: Maximizing effic…
As technology evolves, so do our networks. Today's sprawling network infrastructures are intricate ecosystems, demanding more from IT teams than ever…
Featured Subcategories:
WireShark Articles:
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Your IP address:
216.73.216.176
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Windows Servers
How to Enable ‘Web Server’ Certificate Template Option…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server. …
Windows Servers
Installing Active Directory Services & Domain Controll…
This article serves as an Active Directory tutorial covering installation and setup of Windows 2012 Active Directory Services Role & Domain Controller…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Popular Topics
Windows Servers
How to Enable ‘Web Server’ Certificate Template Option…
In this article we will show you how to enable the ‘Web Server’ certificate template option on a Windows Certification Authority (Windows CA) Server. …
Windows Servers
How to Recover & Create "Show Desktop" Icon Function o…
The Show Desktop feature, included with almost all versions of Windows up to Windows 7, allows a user to minimize or restore all open programs and easily…
Windows Servers
Free Hyper-V eBook - Create, Manage and Troubleshoot Y…
With the introduction of Hyper-V on the Windows Server platform, virtualization has quickly become the de facto standard for all companies seeking to cons…
SASE & SD-WAN Networks
How To Secure Your SD-WAN. Comparing DIY, Managed SD-W…
With so much enterprise network traffic now destined for the cloud, backhauling traffic across an expensive MPLS connection to a data center to apply secu…
Cisco Services & Technologies
WEB SSL VPN - The Next Wave Of Secure VPN Services
Fifteen years ago Virtual Private Networks (VPN) access was a fairly new concept to most businesses. While large corporations already had a good head-star…
Cisco Routers
Configuring PPTP (VPDN) Server On A Cisco Router
The Point to Point Tunneling Protocol (PPTP) is a network protocol used to create VPN tunnels between public networks. These VPN tunnels are encrypted fro…
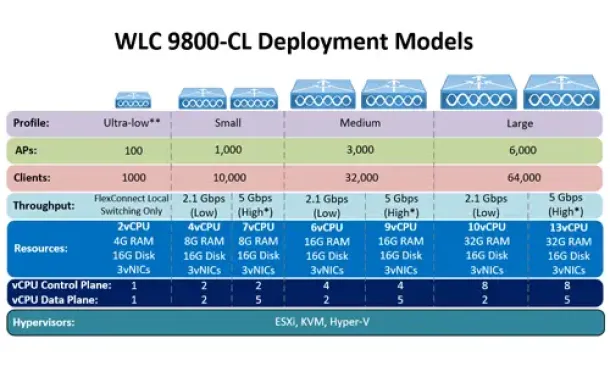
Cisco Wireless
Complete Guide: How to Download & Deploy The Cisco 980…
This article covers the deployment of the Cisco WLC 9800-CL cloud-based controller on the VMware ESXi platform. We explain the CPU, RAM and storage requir…
Cisco Services & Technologies
Troubleshooting Cisco VPN Client Windows 7 - How To Fi…
This article shows how to fix the Cisco VPN Reason 442: Failed to enable Virtual Adapter error on the Windows 7 (32bit or 64bit) operating system. If you…



















