Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobile…
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to pro…
EventLog Analyzer
Detecting Windows Server Security Threats with Ad…
Windows Servers stand as prime targets for hackers and malicious actors due to their widespread usage and historical vulnerabilities. These systems o…

OpManager - Network Monitoring & Management
Optimizing Cisco Router Performance: Best Practic…
Effective monitoring and management of Cisco routers and network devices are essential for ensuring a robust and efficient network infrastructure. In…
Featured Subcategories:
WireShark Articles:
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…

Palo Alto Networks
The Ultimate Guide to Palo Alto Networks Software NGFW…
Discover the ins and outs of using Palo Alto Networks’ Software NGFW (Flex) credits to seamlessly renew your cloud-based or virtualized software NGFW devi…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Windows Servers
Configuring Local Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to efficiently manage a group of people accessing a resource. Group policies can be used to control b…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft Hyper…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET / 10am…
Windows Servers
How to Easily Change Network Card Profile / Network Lo…
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, including…
Windows Servers
How to Enable & Configure Shadow Copy for Shared Folde…
When you shadow copy a disk volume, you are actually generating a snapshot of the changes made to the folders and files within the disk volume at a certai…
Popular Topics

Network Fundamentals
Media Access Control - MAC Addresses
A MAC address, or Media Access Control address, is a unique identifier assigned to a network interface controller (NIC) for use as a network address in…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
In this article, we will cover more advanced DHCP features and topics such as server options, superscopes, multicast scopes, dynamic DNS, DHCP database ba…
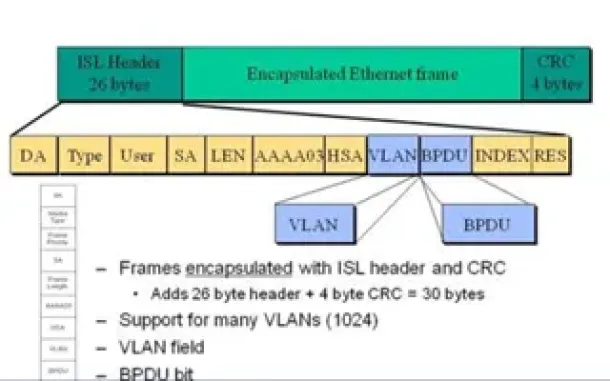
VLAN Networks
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, Torrent…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing processes th…
Cisco Routers
Resolving Cisco Router/Switch Tftp Problems: Source IP…
When working with Cisco equipment that has multiple ip interfaces, a common problem engineers are faced with is trying to successfully tftp to or from the…
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Plus, Plu…
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a num…
Cisco Firewalls
Understand & Configure NAT Reflection, NAT Loopback, H…
This article examines the concept of NAT Reflection, also known as NAT Loopback or Hairpinning, and shows how to configure a Cisco ASA Firewall running AS…

Cisco Data Center (Nexus/UCS)
NEXUS NX-OS: Useful Commands, CLI Scripting, Hints & T…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS using sm…



















