Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With Col…
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addres…
OpManager - Network Monitoring & Management
Network Management Systems Help Businesses Accura…
Accurately monitoring your organization’s business application performance, service provider SLA breaches, network infrastructure traffic, bandwidth…
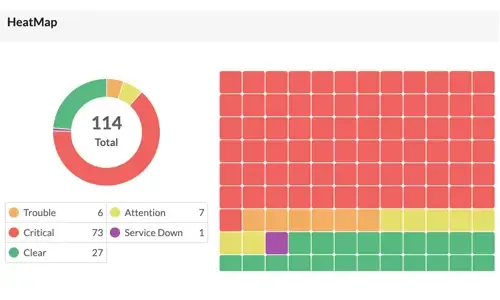
OpManager - Network Monitoring & Management
Boost Network Security and Efficiency with Intell…
Network alerts are vital for maintaining your network's health, efficiency, and security, ensuring seamless daily operations. They act as an early wa…
Featured Subcategories:
WireShark Articles:
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Windows Servers
Understanding, Creating, Configuring & Applying Window…
This article explains what Group Policies are and shows how to configure Windows Server 2012 Active Directory Group Policies. Our next article will cover…
Windows Servers
How to Enable & Configure Shadow Copy for Shared Folde…
When you shadow copy a disk volume, you are actually generating a snapshot of the changes made to the folders and files within the disk volume at a certai…
Windows Servers
Windows Server 2016 VM Backup with Altaro's New VM Bac…
Altaro has released Altaro VM Backup, a faster and lighter upgrade to its flagship Hyper-V and VMware backup solution, which now supports all Windows Serv…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…
Popular Topics
SASE & SD-WAN Networks
How To Secure Your SD-WAN. Comparing DIY, Managed SD-W…
With so much enterprise network traffic now destined for the cloud, backhauling traffic across an expensive MPLS connection to a data center to apply secu…
Windows Servers
How to Easily Change Network Card Profile / Network Lo…
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, including…
Network Fundamentals
Controlling Broadcasts and Multicasts
The first step in controlling broadcast and multicast traffic is to identify which devices are involved in a broadcast or multicast storm. The following p…
Windows Servers
Windows 2016 Server Licensing Explained – Free Webinar
With Windows 2016 Server already making its way into data centers Windows 2016 Server Licensing is becoming a very hot topic. Windows 2016 Server is jam-p…
Cisco CallManager-CCME
Cisco CallManager Express Basic Concepts - Part 2
Our previous article, Cisco CallManager Express Basic Concepts - Part 1 covered the very basic concepts of CCME and its operation. This article continues…
Cisco Firewalls
Cisco ASA 5500 Series Firewall Modules & Cards – Conte…
Cisco’s Adaptive Security Appliance (ASA) Firewalls are one of the most popular and proven security solutions in the industry. Since the introduction of t…
Cisco Routers
Cisco VPN Client Configuration - Setup for IOS Router
Remote VPN access is an extremely popular service amongst Cisco routers and ASA Firewalls. The flexibility of having remote access to our corporate networ…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…



















