Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
Are Cloud-Based Services Overhyped?
| Read |
|
Articles:
What if it Rains in the Cloud?
| Read |
| Read | |
| Read | |
|
Articles:
Email Security - Can't Live Without It!
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
Network Protocol Analyzers
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
Featured Subcategories:
WireShark Articles:
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
How to Perform TCP SYN Flood DoS Attack & Detect…
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and co…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Palo Alto Networks
The Benefits of Palo Alto Networks Firewall Single Pas…
What makes Palo Alto Networks Next-Generation Firewall (NGFW) so different from its competitors is its Platform, Process and Architecture. Palo Alto Netwo…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fire…
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emerging…
Windows Servers
Windows 2012 Server Foundation, Essential, Standard &…
FREE Hyper-V & VMware Virtualization Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Windows Server 2012 Editions…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
Windows Servers
How to Install and Configure Windows 2012 DNS Server R…
Our previous article covered introduction to the Domain Name System (DNS) and explained the importance of the DNS Server role within the network infrastru…
Windows Servers
How to Install/Enable Telnet Client for Windows Server…
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this tool…
Popular Topics
SASE & SD-WAN Networks
How To Secure Your SD-WAN. Comparing DIY, Managed SD-W…
With so much enterprise network traffic now destined for the cloud, backhauling traffic across an expensive MPLS connection to a data center to apply secu…
Network Protocol Analyzers
How to Use Multi-Segment Analysis to Troubleshoot Netw…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubleshoot as…
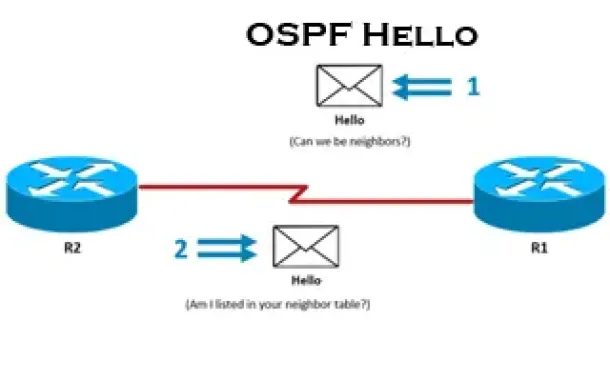
Routing
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…

Virtualization & VM Backup
8 Critical Features to Have in a VM Backup Solution
Businesses that rely on virtual machines for their day-to-day operations should think twice about securing their infrastructure. Modern use of virtual mac…
Cisco CallManager-CCME
Cisco SPA525G / SPA525G2 User Guide Free Download
Available as a free download in our Cisco Small Business Series Product Datasheet section is the Cisco SPA525G / SPA525G2 User Guide. This 68 page user gu…
Cisco CallManager-CCME
How to Upgrade - Update Cisco ATA186 / 188 Firmware a…
The Cisco ATA 186/188 device is well known amongst any Cisco VoIP engineer. It is used allow analog phone devices to connect to the VoIP network and funct…
Cisco Services & Technologies
Introduction to Cisco VIRL – Virtual Internet Routing…
One of the most difficult things for people who are starting out in a networking career is getting their hands on the equipment. Whether you are studying…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…



















