Suggested Articles:
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that wil…
Cisco Routers
Cisco Router Basics
This article will focus on Cisco's routers which can be found in almost any organization due to their popularity and market penetration. Cisco has a…
Cisco Firewalls
Cisco ASA5500 (5505, 5510, 5520, etc) Series Fire…
The Cisco ASA 5500 series security appliances have been around for quite some time and are amongst the most popular hardware firewalls available in t…
Cisco Switches
Cisco Nexus 7000 Series Module Shutdown and Remov…
This article explains the procedure that should be followed to correctly shutdown/powerdown a Cisco Nexus 7000 series module and remove it from the c…
Featured Subcategories:
Data Center Articles:

Introduction to Cisco Nexus Switches – Nexus Prod…
This article introduces the Cisco Nexus product family (Nexus 9000, Nexus 7000, Nexus 5000, Nexus 3000, Nexus 2000, Nexus 1000V and MDS 9000). We exp…

NEXUS NX-OS: Useful Commands, CLI Scripting, Hint…
Whether you’re new to Cisco Nexus switches or have been working with them for years this article will show how to get around the Nexus NX-OS usi…

Nexus 7000/7700 Software Upgrade via ISSU. Comple…
This article shows how to perform an ISSU (In-Service Software Upgrade) on a Nexus Data Center switch (7000 and 7700 models) and avoid service and ne…
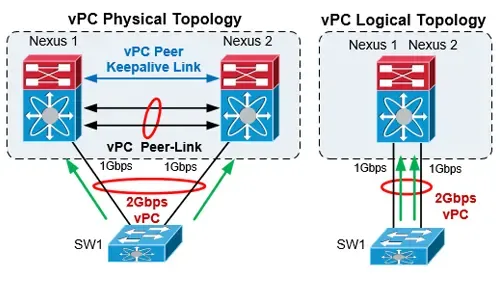
The Complete Cisco Nexus vPC Guide. Features & Ad…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Cisco Switches
Cisco 4507R+E Layer 3 Installation: Redundant WS-X45-S…
It's no news that we here at Firewall.cx enjoy writing about our installations of Cisco equipment and especially devices that we don’t get to see and play…
Cisco Switches
Cisco Catalyst 4500 Series Zero-Downtime IOS Upgrade P…
The Supervisor Engine is the heart of the Cisco Catalyst 4500 and 6500 series switches. It is the equivalent of an engine in a car. Every packet that ente…
Cisco Switches
Complete Guide to DHCP Snooping, How it Works, Concept…
This article covers popular Layer 2 & Layer 3 network attacks with a focus on DHCP Starvation Attacks, Man-in-the-Middle attacks, unintentional rogue…
Cisco Switches
Discover Features & Capabilities - Cisco Catalyst 3850…
There’s a new switch around the block and its name is Catalyst 3850 – Cisco’s latest addition to its successful Catalyst series switches. The Cisco Cataly…
Cisco Firewalls
Converting Cisco Firepower from Platform mode to Appli…
This article explains how to configure a Cisco Firepower 2100 series device to operate in Appliance mode. We’ll show you how to switch from Platform mode…
Cisco Firewalls
Understand & Configure NAT Reflection, NAT Loopback, H…
This article examines the concept of NAT Reflection, also known as NAT Loopback or Hairpinning, and shows how to configure a Cisco ASA Firewall running AS…
Cisco Firewalls
Demystifying Cisco AnyConnect 4.x Licensing. Plus, Plu…
In late 2014, Cisco announced the new licensing model for the latest AnyConnect Secure Mobility client v4.x. With this new version, Cisco introduced a num…
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & Fi…
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and d…
Popular Topics
SASE & SD-WAN Networks
Understanding Secure Access Service Edge (SASE) and ho…
Software Defined Wide Area Networking (SD-WAN) is changing the way that businesses connect to the cloud. With SD-WAN, organizations can move away from clo…
SASE & SD-WAN Networks
SD-WAN is the Emerging, Evolving Solution for the Bran…
A lot has changed in how people work during the past twenty years. Co-working spaces, mobility, and the cloud now are common. Businesses are spread out an…
Virtualization & VM Backup
Differences Between VMware vSphere, vCenter, ESXi Free…
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edition…

Netflow
Netflow: Monitor Bandwidth & Network Utilization. Dete…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, application…



















