Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Firewall.cx Free Cisco Lab: Our Partners
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
Suggested Articles:
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Network Protocol Analyzers
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Featured Subcategories:
WireShark Articles:
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Improve Network Analysis Efficiency with Colasoft…
Troubleshooting network problems can be a very difficult and challenging task. While most IT engineers use a network analyzer to help solve network p…
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Firewalls Security Zones – Tap Zone, Virtual…
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (fire…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo Alt…
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our co…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Windows Servers
Windows 2003 DHCP Server Advanced Configuration - Part…
Part 1 of our Windows 2003 DHCP Server Advanced Configuration article explained the creation and configuration of DHCP Scope options and how to configure…
Windows Servers
Renaming Windows 2000 Domain Name
Sometimes renaming a domain is an essential business requirement. There are many situations, such as mergers, change of company name or migration from a t…
Windows Servers
Windows Server 2016 Licensing Made Easy – Understand Y…
This article describes the new Windows Server 2016 Licensing model (per-core licensing) Microsoft has implemented for its new server-based operating syste…
Windows Servers
Windows 2003 DNS Server Installation & Configuration
DNS is used for translating host names to IP addresses and the reverse, for both private and public networks (i.e.: the Internet). DNS does this by using…
Popular Topics
Network Fundamentals
Network Broadcast
The term "Broadcast" is used very frequently in the networking world . You will see it in most networking books and articles, or see it happening on your…
SASE & SD-WAN Networks
MPLS vs. SD-WAN vs. Internet vs. Cloud Network. Connec…
The Wide Area Network (WAN) is the backbone of the business. It ties together the remote locations, headquarters and data centers into an integrated netwo…

Network Fundamentals
Securing Your Home Network
In today's world, securing your home network is more important than ever. With the increasing number of cyberattacks, data breaches, and online frauds, pr…
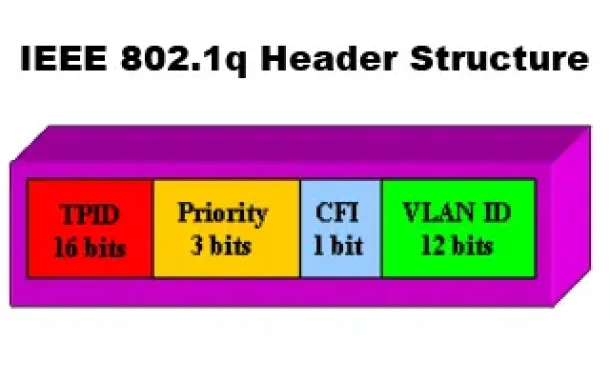
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
Cisco Routers
How and Why You Should Verify IOS Images On Cisco Rout…
Chances are we’ve all needed to upgrade our Cisco’s device IOS software at some point. While upgrading the IOS software on a Cisco device is considered to…
Cisco Services & Technologies
Comparing Cisco VPN Technologies – Policy Based vs Rou…
Virtual Private Networks constitute a hot topic in networking because they provide low cost and secure communications between sites (site-to-site VPNs) wh…
Cisco Routers
Enabling & Configuring SSH on Cisco Routers. Restrict…
This article shows how to configure and setup SSH for remote management of Cisco IOS Routers. We’ll show you how to check if SSH is supported by your IOS…
Cisco Services & Technologies
The Cisco Smart Care Service & Appliance
Cisco, as most IT engineers know, covers a wide range of products and services. These range from routers to switches, firewalls, intrusion prevention syst…



















