Network Management Articles:
OpManager - Network Monitoring & Management
Ensuring Enterprise Network Readiness for Mobil...
Demands for Enterprise networks to properly support mobile users is on a continuous rise making it more than ever necessary for IT departments to provide high-quality services to its users. This ar...
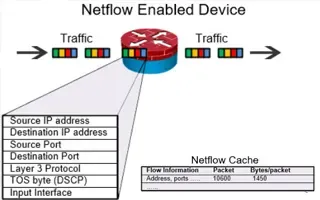
Netflow
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive into the technical details of how the Netflow proto...

Netflow
Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, application traffic and data flows allows network engi...

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rul...
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance of cybersecurity cannot be overstated. Among th...
Featured Subcategories:
Network Protocol Analyzer Articles:
Network Protocol Analyzers
Introducing Colasoft Unified Performance Manage...
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quality, fault, and security issues based on business...
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, ...
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing processes that not only consumes valuable bandwidth, bu...
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC address and responding on their behalf, while at the s...
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor ...
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis application that captures packets/data around the cl...
Virtualization & VM Backup:
Virtualization & VM Backup
Understanding Deduplication. Complete Guide to ...
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective but also an operational one. While is it true that ...
Virtualization & VM Backup
Differences Between VMware vSphere, vCenter, ES...
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edition: vSphere Standard, Enterprise plus and Plant...
Virtualization & VM Backup
FREE Webinar - Fast Track your IT Career with V...
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladder in the IT industry is usually dependent on on...
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities ...
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The good news is that there are plenty of ways a...
Firewall Articles:
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap M...
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the different configuration options for physica...
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA ...
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and data centers from today’s advanced security ...
Cisco Firewalls
Cisco ASA Firepower Threat Defense (FTD): Downl...
One Appliance – One Image is what Cisco is targeting for its Next Generation Firewalls. With this vision, Cisco has created a unified software image named “Cisco Firepower Threat Defense”. In...
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall ...
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, safe from known vulnerabilities and exploits b...
Your IP address:
18.116.85.72
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Top Picks
Windows Servers
Easy, Fast & Reliable Hyper-V & VMware Backup with Altaro's Free Backup Solution
As more companies around the world adopt the virtualization technology to increase efficiency and productivity, Microsoft’s Hyper-V virtualization ...
SASE & SD-WAN Networks
Configuring A SASE Unified Network: Data centers, Remote Sites, VPN Users, and more
This article explores the need for Secure Access Service Edge (SASE) in today’s organizations. We show how one of the most advanced SASE platforms ...
Security Service Edge (SSE)
Security Service Edge (SSE) Limitations & Disadvantages. Protecting all Traffic, Users, Apps, and Services with 360-degree SSE
This article explores the Security Service Edge (SSE) portion of Secure Access Service Edge (SASE) and the need for holistic cybersecurity protecti...
Virtualization & VM Backup
Understanding Deduplication. Complete Guide to Deduplication Methods & Their Impact on Storage and VM Backups
When considering your VM backup solution, key features such as deduplication are incredibly important. This is not simply from a cost perspective b...




















