Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Direct Cable Connection
| Read |
| Read | |
| Read | |
| Read | |
|
Articles:
Important Direct Cable Connection Notes
| Read |
| Read | |
|
Articles:
100Base-(T) TX/T4/FX - Ethernet
| Read |
|
Articles:
10Base-T/2/5/F/35 - Ethernet
| Read |
| Read | |
|
Articles:
Straight Thru UTP Cables
| Read |
| Read | |
Suggested Articles:
Subnetting
IP Subnetting - Part 1: The Basic Concepts
When we subnet a network, we basically split it into smaller networks. For example, when a set of IP Addresses is given to a company, e.g 254 they ...
Network Protocols
IPv6 - Analysing the IPv6 Protocol Structure an...
As discussed in the previous tutorial, we were made painfully aware that we were running out of IP address spaces and literally did in 2011. A ne...
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 2: TCP Sequence &...
This page will closely examine the Sequence and Acknowledgement numbers. The very purpose of their existence is related directly to the fact that t...
Network Cabling
Straight Thru UTP Cables
This article covers the commonly known Unshielded Twisted Pair (UTP) cable and shows how many pairs the UTP Cat5, Cat5e, Cat6 & Cat7 cables con...
Featured Subcategories:
Netflow Articles:
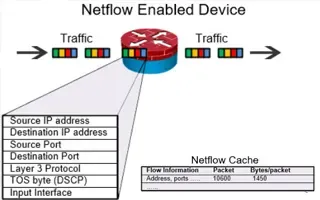
Complete Guide to Netflow: How Netflow & its Co...
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive i...
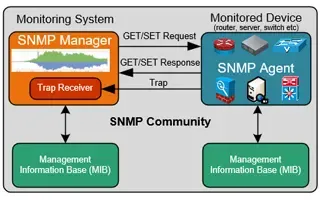
Netflow vs SNMP. Two Different Approaches to Ne...
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ...
NetFlow Analyzer: Free Download, Step-by-Step I...
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows...

Netflow: Monitor Bandwidth & Network Utilizatio...
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, appl...
Your IP address:
3.138.110.119
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trun...

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article an...

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Ne...

VLAN Networks
Dynamic VLANs
Dynamic VLANs were introduced to grant the flexibility and complexity(!) that Static VLANs did not provide. Dynamic VLANs are quite rare because of thei...
Routing
Hybrid Routing Protocols - Advantages and Disadvanta...
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scala...
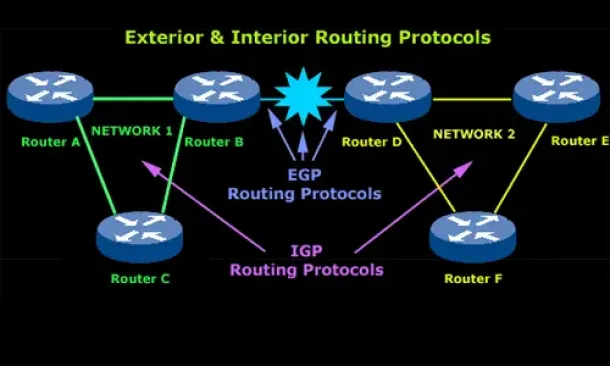
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchan...
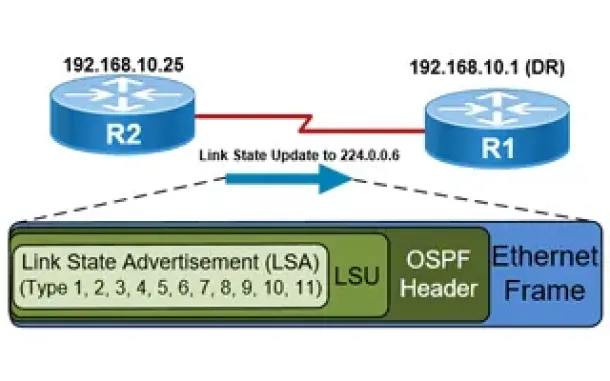
Routing
OSPF - Part 5: Analysis of OSPF Link State Update (L...
This article explains how OSPF uses Link State Advertisement (LSA) to exchange information about the network topology between routers. When a router rec...
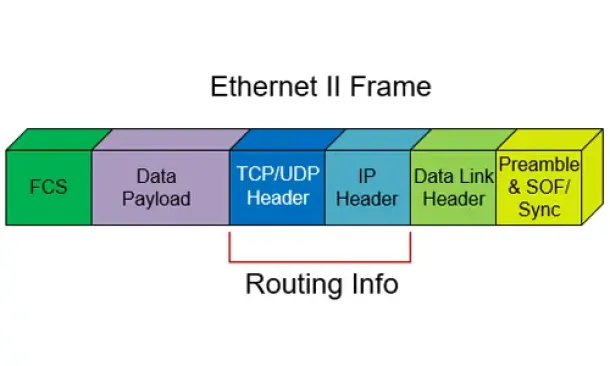
Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other a...
Cisco Wireless
Easily Convert Cisco Autonomous - Standalone AP to L...
This article explains how to convert a local or remote Autonomous / Standalone Cisco Aironet Access Point to Lightweight and register it to a Cisco WLC ...
Cisco Routers
Cisco Type 7 Password Decrypt / Decoder / Crack Tool
The Firewall.cx Cisco Password Decoder Tool (see below) provides readers with the ability to decrypt 'Type 7' cisco passwords.
For security reasons, we...
Cisco Routers
How To Secure Your Cisco Router Using Cisco AutoSecu...
In today’s complex network environments securing your network routers can be a daunting task, especially when there are so many CLI commands and paramet...
Cisco Wireless
Cisco Aironet 1100 & 1200 Series (1110, 1121, 1142, ...
Resetting a Cisco Aironet access point can be required if you’ve lost your password or need to wipe out the configuration of a previously configured acc...




















