Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
|
Articles:
VLAN Security - Making the Most of VLANs
| Read |
|
Articles:
VTP Pruning
| Read |
|
Articles:
VTP Protocol - In-Depth Analysis
| Read |
|
Articles:
VTP Introduction & Modes
| Read |
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
VLANs - Access & Trunk Links
| Read |
|
Articles:
Dynamic VLANs
| Read |
|
Articles:
Static VLANs
| Read |
| Read | |
|
Articles:
The VLAN Concept - Introduction to VLANs
| Read |
Suggested Articles:
ICMP Protocol
ICMP Protocol - Part 7: Time Exceeded Message Ana…
The ICMP - Time Exceeded message is one which is usually created by gateways or routers. In order to fully understand this ICMP message, you must be…
Network Cabling
Serial Direct Cable Connection, DB9, DB25, COM Po…
This article covers the popular serial ports on workstations, servers and laptop computers. We cover serial data transfer, port pinouts, port speeds…

Network Fundamentals
Need for Speed – The Data Tsunami & Advancements…
A long-long time ago (not long ago in earth time) 100 Mbps was THE technology. 100 Mbps uplinks bundled with ether-channel was the ultimate uplink te…
Network Cabling
1Gigabit 802.3ab -10GBase (10Gigabit) 802.3an Eth…
The 1000Base Ethernet standard, also referred to as Gigabit Ethernet (GbE or 1GigE) is defined by the IEEE 802.3-2008 standard and provides 10 times…
Featured Subcategories:
Netflow Articles:
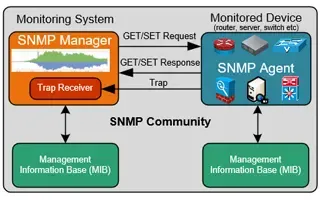
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
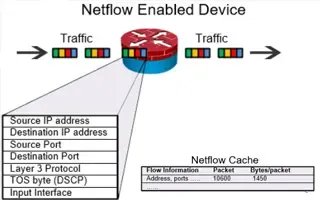
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
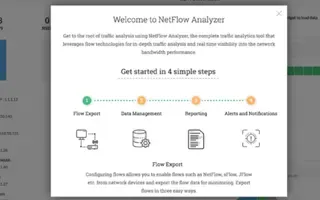
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
VLAN Networks
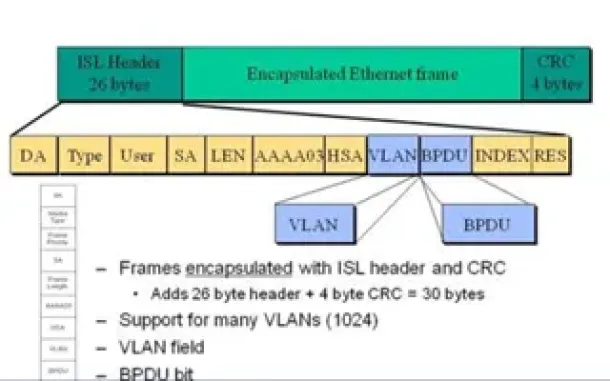
VLAN InterSwitch Link (ISL) Protocol Analysis
Deciding whether to use ISL or IEEE 802.1q to power your trunk links can be quite confusing if you cannot identify the advantages and disadvantages of eac…

VLAN Networks
VTP Protocol - In-Depth Analysis
The previous article introduced the VTP protocol, we examined how it can be used within a network, to help manage VLANs and ease the administrative overhe…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
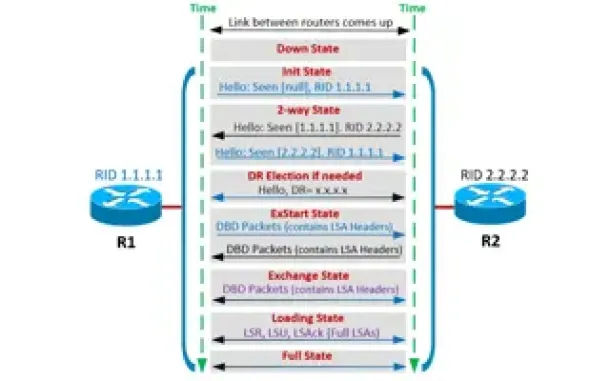
Routing
OSPF - Part 4: OSPF Neighbor States – OSPF Neighbor Fo…
This is the third article of our OSPF series which analyzes the different OSPF States routers go through during the OSPF discovery and neighbor forming pr…
Routing
Enhanced Interior Gateway Routing Protocol - EIGRP
Enhanced Interior Gateway Routing Protocol (EIGRP), similar to IGRP, is a Cisco proprietary routing protocol that is used to exchange routing information…
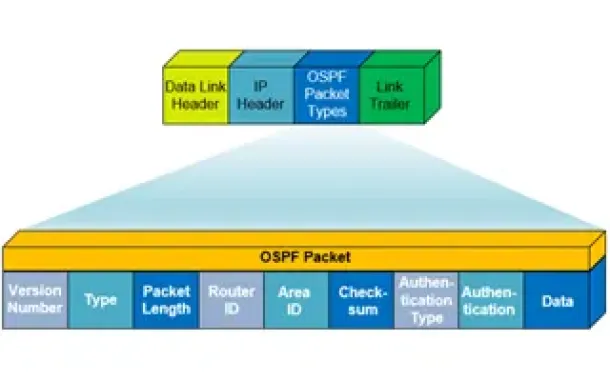
Routing
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
Hybrid Routing Protocols - Advantages and Disadvantage…
Hybrid routing protocols are a combination of distance-vector and link-state routing protocols, and are used to provide a more efficient and scalabl…
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server running…
Cisco Wireless
Wireless (Wifi) WEP WPA WPA2 Key Generator
The Firewall.cx Wireless LAN Key Generator will allow the generation of a WEP or WPA ASCII based encryption key and will provide the equivalent HEX or…
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities Reveale…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The g…
SASE & SD-WAN Networks
Complete Guide to SD-WAN. Technology Benefits, SD-WAN…
SD-WAN is the answer for enterprises and organizations seeking to consolidate network functions and services while at the same time simplify their WAN inf…



















