Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
|
Articles:
The OSI Model: Layer 5 - Session Layer
| Read |
|
Articles:
The OSI Model: Layer 4 - Transport Layer
| Read |
|
Articles:
The OSI Model: Layer 3 - Network Layer
| Read |
|
Articles:
The OSI Model: Layer 2 - Datalink Layer
| Read |
|
Articles:
The OSI Model: Layer 1 - Physical Layer
| Read |
Suggested Articles:
Network Protocols
Introduction To The ISDN Protocol
ISDN (Integrated Services Digital Network) is a digital telephone standard designed to replace analogue connections by utilising ordinary copper wire…
Ethernet Protocol, CSMA/CD, Collisions
Ethernet Troubleshooting - Physical Frame Corrupt…
When troubleshooting your Ethernet network, the first thing to look for is physical frame corruption. In this essay, we will discuss the different ca…
Network Address Translation - NAT
The Network Address Translation Table
After that simple and informative introduction to the NAT concept, it's time to find out more about how it works and this is where the NAT table come…
Network Protocols
IPv6 - Analysing the IPv6 Protocol Structure and…
As discussed in the previous tutorial, we were made painfully aware that we were running out of IP address spaces and literally did in 2011. A new…
Featured Subcategories:
Netflow Articles:
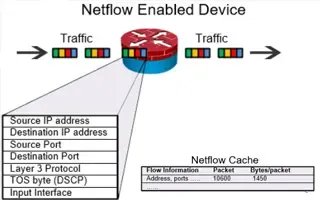
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
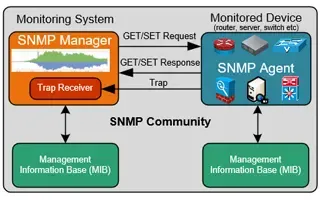
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
Static VLANs
VLANs are usually created by the network administrator, assigning each port of every switch to a VLAN. Depending on the network infrastructure and securit…

VLAN Networks
InterVLAN Routing - Routing between VLAN Networks
This article deals with the popular topic of InterVLAN routing, which is used to allow routing & communication between VLAN networks. Our article anal…

VLAN Networks
VLANs - Access & Trunk Links
If you've read our previous article The VLAN Concept - Introduction to VLANs then you should feel comfortable with terms such as 'VLAN', 'Stati…
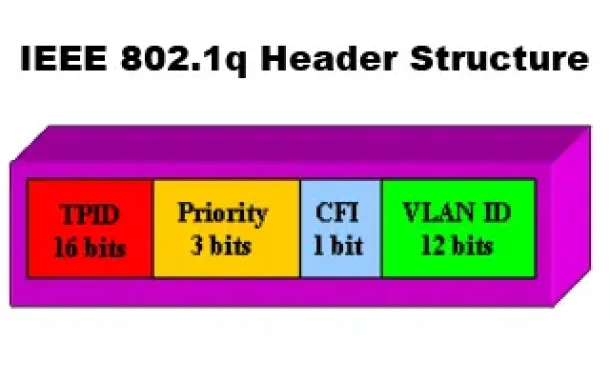
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…
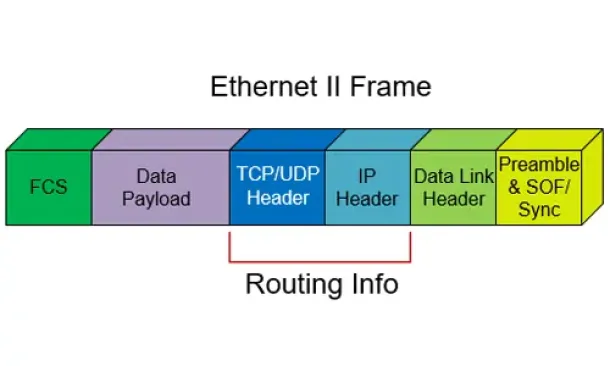
Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other and…
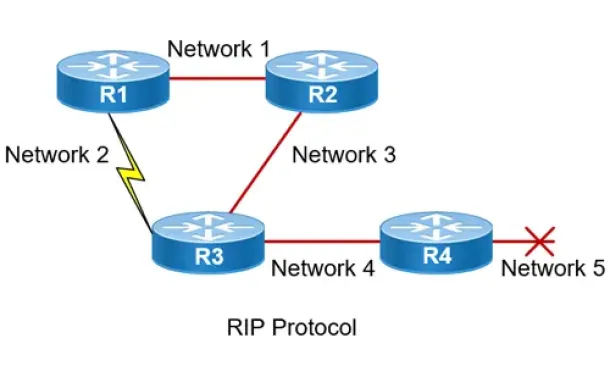
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
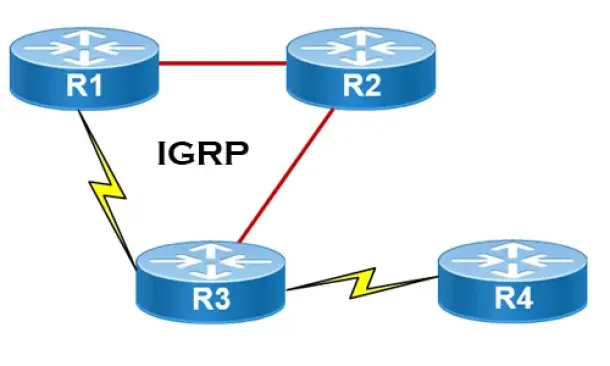
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
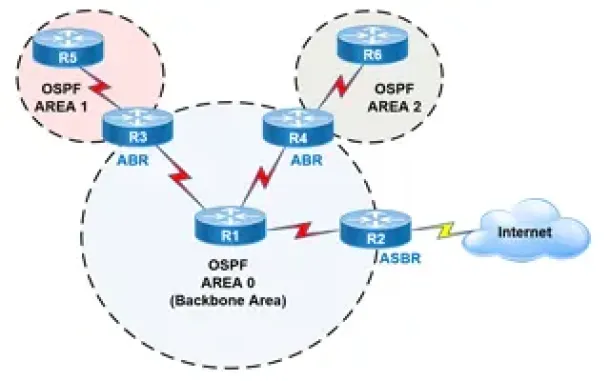
Routing
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
Windows Servers
Free Webinar: Migrating from Hyper-V to VMware
If your organization is planning to migration from a Hyper-V virtualization environment to VMware then this FREE webinar is just for you.
Aimed toward Hy…
Cisco Switches
Cisco Catalyst Err-disabled Port State, Enable & Disab…
Errdisable is a feature that automatically disables a port on a Cisco Catalyst switch. When a port is error disabled, it is effectively shut down and…
Windows Servers
Windows 2003 DHCP Server Installation & Configuration
DHCP (Dynamic Host Configuration Protocol) is a protocol that allows clients on a network to request network configuration settings from a server running…
Cisco Firewalls
Cisco ASA 5500-X Series Firewall with IPS, ASA CX & Fi…
The Cisco ASA Firewall 5500-X series has evolved from the previous ASA 5500 Firewall series, designed to protect mission critical corporate networks and d…



















