Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
|
Articles:
802.3 Fast Ethernet (100 Mbit/Sec) Model
| Read |
|
Articles:
Migrating From Ethernet To Fast Ethernet
| Read |
| Read | |
| Read | |
|
Articles:
The Novell Proprietary Frame Format
| Read |
|
Articles:
The IEEE 802.3 SNAP Frame Format
| Read |
|
Articles:
The Ethernet II Frame Format
| Read |
|
Articles:
The IEEE 802.3 Frame Format
| Read |
|
Articles:
Manchester Signal Encoding
| Read |
|
Articles:
IEEE 802.3 Interframe Spacing
| Read |
| Read | |
|
Articles:
Propagation Delay
| Read |
|
Articles:
Late Ethernet Collisions
| Read |
|
Articles:
Early Ethernet Collisions
| Read |
|
Articles:
Introduction to Ethernet Collisions
| Read |
|
Articles:
What is CSMA/CD ?
| Read |
Suggested Articles:
Supernetting & CIDR
Supernetting In-Depth Analysis - Learn to Identif…
Our previous article served as an introduction to Supernetting, also known as Route Summarization. We covered the concept of Supernetting, how it wor…

Network Fundamentals
DoS & DDoS Attacks
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, server or network by flooding it with traffic…
Domain Name System (DNS)
The DNS Protocol - Part 4: DNS Response Message F…
The previous article covered the DNS Query message formats. In the article we analysed them in great detail and showed how various options are select…
Network Cabling
Straight Thru UTP Cables
This article covers the commonly known Unshielded Twisted Pair (UTP) cable and shows how many pairs the UTP Cat5, Cat5e, Cat6 & Cat7 cables consi…
Featured Subcategories:
Netflow Articles:
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
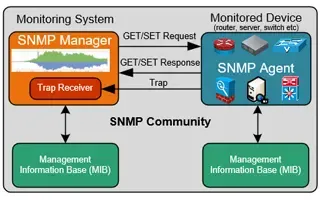
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
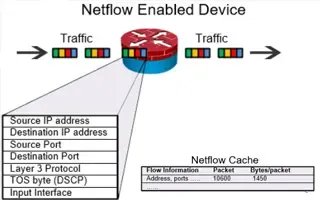
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…
VLAN Networks
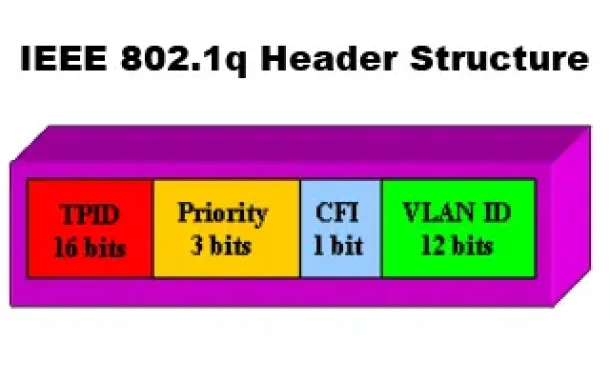
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…

VLAN Networks
Comparing Traditional Flat & VLAN Networks
Designing and building a network is not a simple job. VLANs are no exception to this rule, in fact they require a more sophisticated approach because of t…
Routing
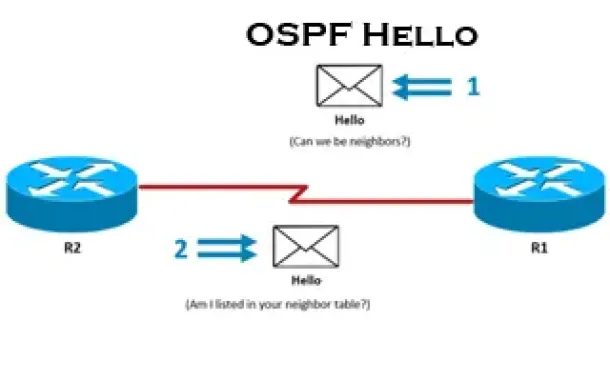
OSPF - Part 3: OSPF Adjacency & Neighbor Forming Proce…
This is the thrid article of our 6-part OSPF series (see below) that describes how OSPF routers perform neighbor relationship and adjacency. We’ll examine…
Routing
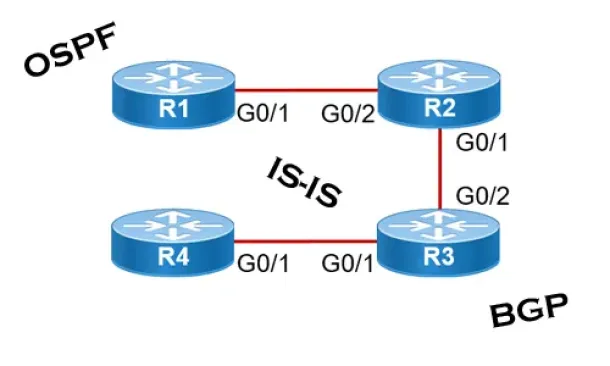
Link State Routing Protocols
Link State routing protocols do not view networks in terms of adjacent routers and hop counts, but they build a comprehensive view of the overall network…
Routing
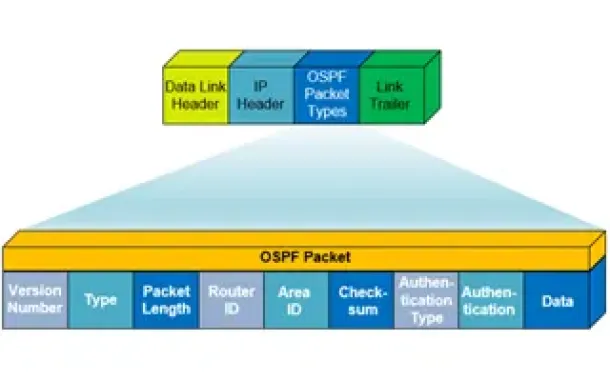
OSPF - Part 1: Introduction, OSPF Packet Structure, OS…
Open Shortest Path First (OSPF) is a popular routing protocol developed for Internet Protocol (IP) networks by the Interior Gateway Protocol (IGP) working…
Routing
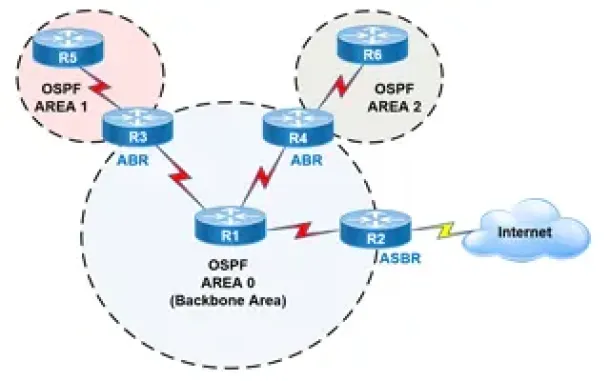
OSPF - Part 2: How OSPF Protocol Works & Basic Concept…
This article covers basic OSPF concepts and operation. We explain how OSPF works, how OSPF tables are built on an OSPF-enabled router and their purpose (N…
Palo Alto Networks
How to Register a Palo Alto Firewall and Activate Supp…
This article explains how to register and activate your Palo Alto Firewall Appliance to obtain technical support, RMA hardware replacement, product update…
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. Analys…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual machine…
Virtualization & VM Backup
5 Most Critical Microsoft M365 Vulnerabilities Reveale…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data. The g…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…



















