Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
|
Articles:
Direct Cable Connection
| Read |
| Read | |
| Read | |
| Read | |
|
Articles:
Important Direct Cable Connection Notes
| Read |
| Read | |
|
Articles:
100Base-(T) TX/T4/FX - Ethernet
| Read |
|
Articles:
10Base-T/2/5/F/35 - Ethernet
| Read |
| Read | |
|
Articles:
Straight Thru UTP Cables
| Read |
| Read | |
Suggested Articles:
TCP - UDP Protocol Analysis
TCP Header Anaylsis - Section 3: TCP Header Lengt…
The third field under close examination is the TCP Header length. There really isn't that much to say about the Header length other than to explain w…
IP Protocol
IP Protocol - Part 2: The Internet Protocol (IP)…
This article examines the Internet Protocol (IP) and its position within the OSI Model. We take a look at the IP Header and all fields contained with…
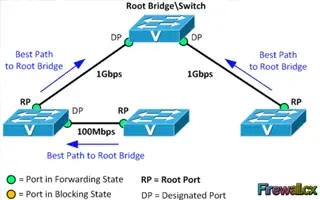
Spanning Tree Protocol (STP)
Spanning Tree Protocol – Part 2: Rapid STP Port C…
Spanning Tree Protocol, Rapid STP port costs and port states are an essential part of the STP algorithm that affect how STP decides to forward or blo…
Network Protocols
Introduction To The ISDN Protocol
ISDN (Integrated Services Digital Network) is a digital telephone standard designed to replace analogue connections by utilising ordinary copper wire…
Featured Subcategories:
Netflow Articles:
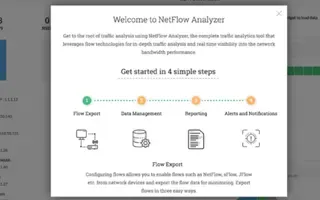
NetFlow Analyzer: Free Download, Step-by-Step Ins…
In our previous article we explained how a Netflow Analyzer can help you gain visibility into your user traffic, application traffic and data flows w…
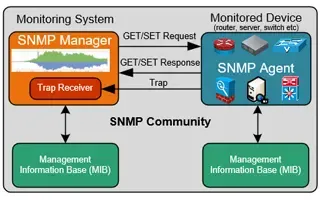
Netflow vs SNMP. Two Different Approaches to Netw…
SNMP (Simple Network Management Protocol) and Netflow are both popular protocols with admins, prized for their ability to give visibility over the ne…
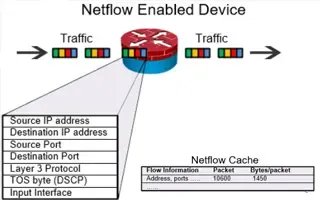
Complete Guide to Netflow: How Netflow & its Comp…
This article will cover the basics of Netflow, including its use cases, Netflow supported devices, Netflow history, and variants. We’ll also dive int…

Netflow: Monitor Bandwidth & Network Utilization…
Monitoring network traffic & bandwidth usage via Netflow is mandatory for any type and size network. Gaining visibility into user traffic, applic…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
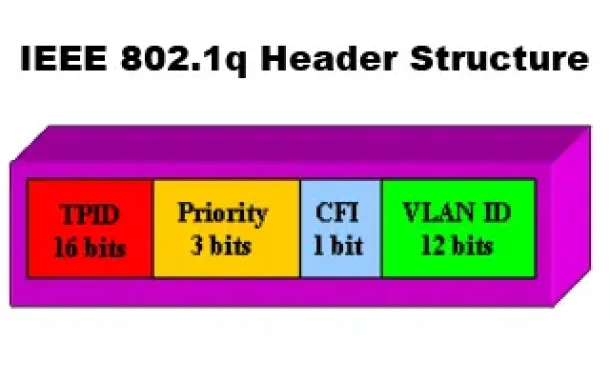
VLAN Networks
VLANs - IEEE 802.1q Trunk Link Protocol Analysis
While the VLAN Tagging article briefly covered the IEEE 802.1q protocol this article will continue building upon it by further analyzing the IEEE 802.1q T…

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network wi…

VLAN Networks
The VLAN Concept - Introduction to VLANs
We hear about them everywhere, vendors around the world are constantly trying to push them into every type of network and as a result, the Local Area Netw…

VLAN Networks
VTP Pruning
VTP (VLAN Trunking Protocol) pruning is a feature that is used in Cisco switches to reduce unnecessary traffic in VLAN (Virtual Local Area Network) trunks…
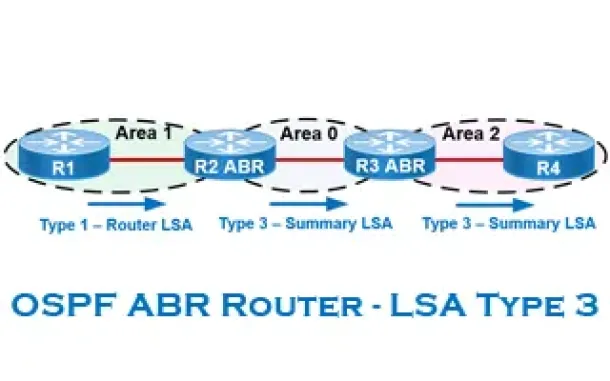
Routing
OSPF - Part 6: OSPF LSA Types - Purpose and Function o…
Our previous article explained the purpose of Link State Update (LSU) packets and examined the Link State Advertisement (LSA) information contained within…
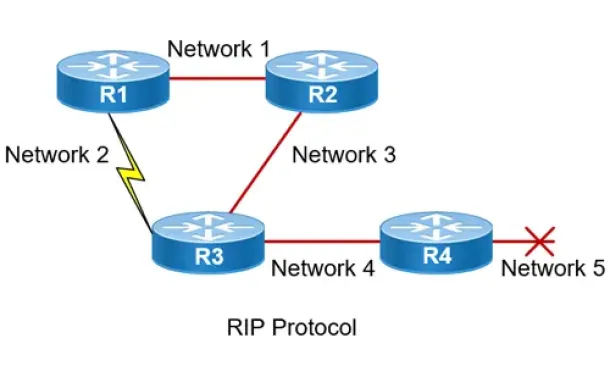
Routing
Routing Information Protocol - RIP
Routing Information Protocol (RIP) is a distance-vector routing protocol that is commonly used in small to medium-sized networks. It is one of the o…
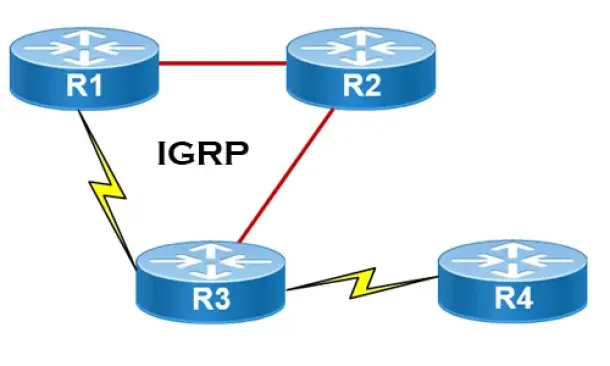
Routing
Interior Gateway Protocol - IGRP
IGRP (Interior Gateway Routing Protocol) is a Cisco proprietary distance-vector routing protocol used in enterprise networks to exchange routing informati…
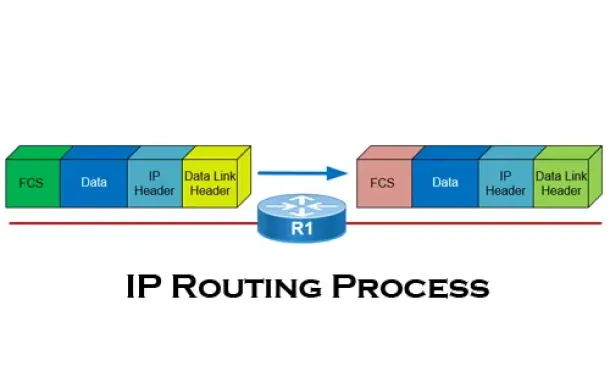
Routing
The IP Routing Process - Step-by-Step Analysis
We are going to analyse what happens when routing occurs on a network (IP routing process). When I was new to the networking area, I thought that all you…

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Network Protocol Analyzers
Detect Brute-Force Attacks with nChronos Network Secur…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/database…
Cisco Switches
How to Disable or Enable the Password Recovery Procedu…
Our previous article shows how to perform a password recovery on the Cisco Catalyst switches. This article will now explain how to disable or enable the C…
Cisco Switches
VLAN Security Tips - Best Practices
This article focuses on VLAN Security and its implementation within the business network environment. We provide tips and Cisco CLI commands that will hel…



















