Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
MS Server Articles:
Windows Servers
Creating a Virtual Machine in Windows Hyper-V. Co…
Our previous articles covered basic concepts of Virtualization along with the installation and monitoring of Windows 2012 Hyper-V. This article takes…
Windows Servers
Windows 2003 DNS Server Installation & Configurat…
DNS is used for translating host names to IP addresses and the reverse, for both private and public networks (i.e.: the Internet). DNS does this by u…
Windows Servers
Windows Server 2016 – Hyper-V Virtualization Upda…
The new Hyper-V virtualization features offered by Windows Server 2016 are planning to make major changes in the virtualization market. From Nested H…
Windows Servers
Active Directory Tombstone Lifetime Modification
Tombstone is a container object that contains the deleted objects from Active Directory. Actually when an object is deleted from Active Directory, it…
Featured Subcategories:
Virtualization & VM Backup Articles:

8 Critical Features to Have in a VM Backup Soluti…
Businesses that rely on virtual machines for their day-to-day operations should think twice about securing their infrastructure. Modern use of virtua…
SysAdmin Day 2020 - Get your Free Amazon Voucher…
SysAdmin Day has arrived, and with it, gratitude for all the unsung heroes that 2020 has needed. Your hard work has made it possible for all of us to…
The Backup Bible. A Free Complete Guide to Disast…
The Free Backup Bible Complete Edition written by backup expert and Microsoft MVP Eric Siron, is comprised of 200+ pages of actionable content divide…
FREE Webinar - Fast Track your IT Career with VMw…
Everyone who attends the webinar has a chance of winning a VMware VCP course (VMware Install, Config, Manage) worth $4,500!
Climbing the career ladd…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Linux CentOS - Redhat EL Installation on HP Smart Arra…
This article was written thanks to our recent encounter of a HP DL120 G7 rack mount server equipped with a HP Smart Array B110i SATA Raid controller, need…
Linux - Unix
Understanding, Administering Linux Groups and User Acc…
In a multi-user environment like Linux, every file is owned by a user and a group. There can be others as well who may be allowed to work with the file. W…
Linux - Unix
Installing & Configuring Linux Webmin - Linux Web-Base…
For many engineers and administrators, maintaining a Linux system can be a daunting task, especially if there’s limited time or experience. Wo…
Linux - Unix
Installing & Configuring VSFTPD FTP Server for Redhat…
Vsftpd is a popular FTP server for Unix/Linux systems. For thoes unaware of the vsftpd ftp server, note that this is not just another ftp server, but a ma…
Popular Topics
Cisco Routers
Configuring Policy-Based Routing (PBR) with IP SLA Tra…
What is Policy-Based Routing?
Policy-Based Routing (PBR) is a very popular feature in Cisco routers, it allows the creation of policies that can selectiv…
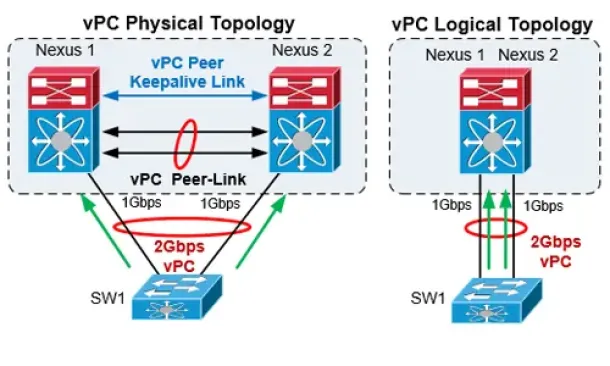
Cisco Data Center (Nexus/UCS)
The Complete Cisco Nexus vPC Guide. Features & Advanta…
Cisco virtual Port Channel (vPC) is a virtualization technology, launched in 2009, which allows links that are physically connected to two different Cisco…
Cisco Routers
How to Restrict Cisco IOS Router VPN Client to Layer-4…
In our article Cisco VPN Client Configuration - Setup for IOS Router we explained how to setup up a Cisco IOS router to support Cisco IPSec VPN clie…
Cisco Switches
Spanning Tree BPDU Guard and Errdisable Interface Auto…
Running Spanning Tree Protocol (STP) in a large network environment can be a challenging task especially when features/enhancements such as BPDU Filter an…


















