Configuring Local Group Policy for Windows 2003
Windows 2003 Group Policies allow the administrators to efficiently manage a group of people accessing a resource. Group policies can be used to control both the users and the computers.
They give better productivity to administrators and save their time by allowing them to manage all the users and computers centrally in just one go.
Group policies are of two types, Local Group Policy and Domain-based Group Policy. As the name suggests, Local Group Policies allow the local administrator to manage all the users of a computer to access the resources and features available on the computer. For example an administrator can remove the use of the Run command from the start menu. This will ensure that the users will not find Run command on that computer.
Domain-based Group Policies allow the domain / enterprise administrators to manage all the users and the computers of a domain / forest centrally. They can define the settings and the allowed actions for users and computers across sites, domains and OUs through group policies.
There are more than 2000 pre-created group policy settings available in Windows Server 2003 / Windows XP. A default group policy already exists. You only need to modify the values of different policy settings according to your specific requirements. You can create new group policies to meet your specific business requirements. Group policies allow you to implement:
Registry based settings: Allows you to create a policy to administer operating system components and applications.
Security settings: Allows you to set security options for users and computers to restrict them to run files based on path, hash, publisher criteria or URL zone.
Software restrictions: Allows you to create a policy that would restrict users running unwanted applications and protect computers against virus and hacking attacks.
Software distribution and installation: Allows you to either assign or publish software application to domain users centrally with the help of a group policy.
Roaming user profiles: Allows mobile users to see a familiar and consistent desktop environment on all the computers of the domain by storing their profile centrally on a server.
Internet Explorer maintenance: Allows administrators to manage the IE settings of the users' computers in a domain by setting the security zones, privacy settings and other parameters centrally with the help of group policy.
Using Local Group Policy
Local Group Policies affect only the users who log in to the local machine but domain-based policies affect all the users of the domain. If you are creating domain-based policies then you can create policy at three levels: sites, domains and OUs. Besides, you have to make sure that each computer must belong to only one domain and only one site.
A Group Policy Object (GPO) is stored on a per domain basis. However, it can be associated with multiple domains, sites and OUs and a single domain, site or OU can have multiple GPOs. Besides this, any domain, site or OU can be associated with any GPO across domains.
When a GPO is defined it is inherited by all the objects under it and is applied in a cumulative fashion successively starting from local computer to site, domain and each nested OU. For example if a GPO is created at domain level then it will affect all the domain members and all the OUs beneath it.
After applying all the policies in hierarchy, the end result of the policy that takes effect on a user or a computer is called the Resultant Set of Policy (RSoP).
To use GPOs with greater precision, you can apply Windows Management Instrumentation (WMI) filters and Discretionary Access Control List (DACL) permissions. The WMI filters allow you to apply GPOs only to specific computers that meet a specific condition. For example, you can apply a GPO to all the computers that have more than 500 MB of free disk space. The DACL permissions allow you to apply GPOs based on the user's membership in security groups.
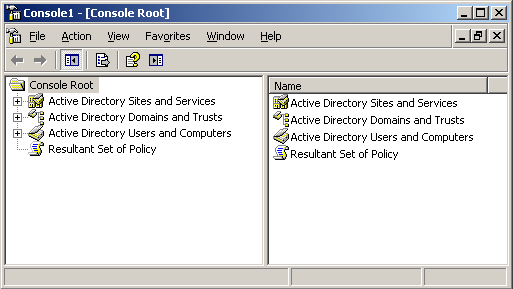
Windows Server 2003 provides a GPMC (Group Policy Management Console) that allows you to manage group policy implementations centrally. It provides a unified view of local computer, sites, domains and OUs (organizational units). You can have the following tools in a single console:
- Active Directory Users and Computers
- Active Directory Sites and Services
- Resultant Set of Policy MMC snap-in
- ACL Editor
- Delegation Wizard
The screenshot below shows four tools in a single console.
A group policy can be configured for computers or users or both, as shown here:
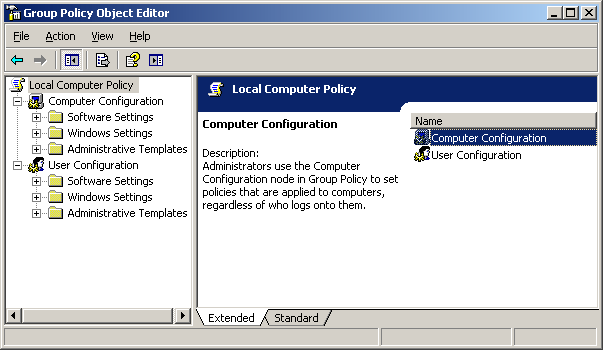
The Group Policy editor can be run using the gpedit.msc command.
Both the policies are applied at the periodic refresh of Group Policies and can be used to specify the desktop settings, operating system behavior, user logon and logoff scripts, application settings, security settings, assigned and published applications options and folder redirection options.
Computer-related policies are applied when the computer is rebooted and User-related policies are applied when users log on to the computer.
Configuring a Local Group Policy
To configure a local group policy, you need to access the group policy editor. You can use Group Policy Editor by logging in as a local administrator from any member server of a domain or a workgroup server but not from a domain controller.
Sometimes this tool, or other Active directory tools that you need to manage group policy, does not appear in Administrative Tools. In that case you need to follow steps 1-10 given below to add Group Policy Editor tool in the console.
1. Click Start->Run and type mmc. The Console window appears, as shown below:
2. Select Add/remove Snap-in from the File menu.
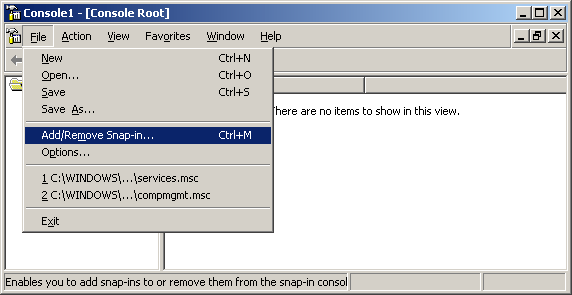
The Add/Remove Snap-in window appears, as shown below:
3. Click Add.
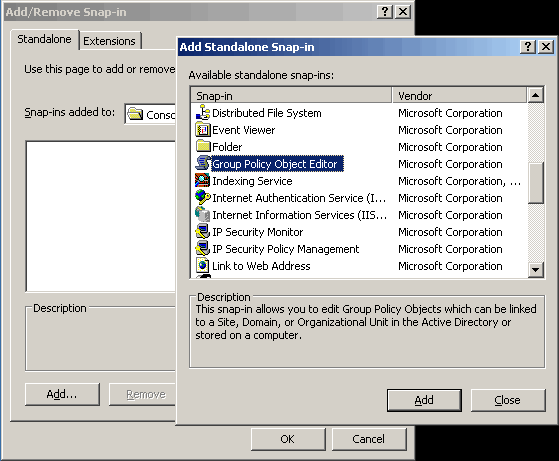
4. The Add Standalone Snap-in window appears.
5. Select Group Policy Object Editor snap-in from the list.
6. Click Add and then click OK in Add/remove Snap-in window.
The Select Group Policy Object window appears, as shown below:
7. Keep the default value “Local Computer”
8. Click Finish.
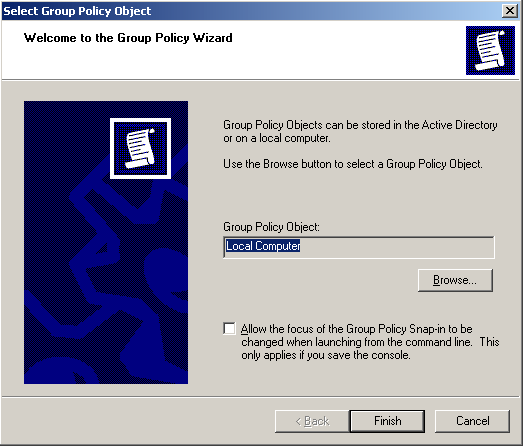
The Local Computer Policy MMC appears, as shown below.
You can now set the Computer Configuration or User Configuration policies as desired. This example takes User Configuration setting.
9. Expand User Configuration node:
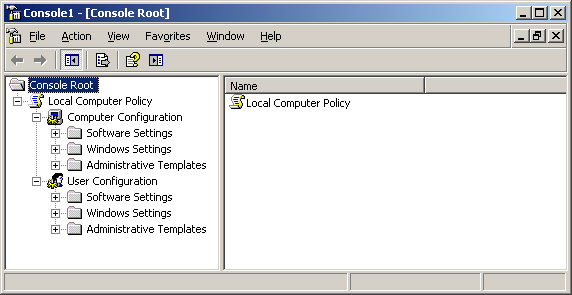
10. Expand Administrative Templates and then select the Start Menu and Taskbar node, as shown in Figure 7.
11. Double-click the settings for the policy that you want to modify from the right panel. In this example double-click Remove Run Menu from Start Menu.
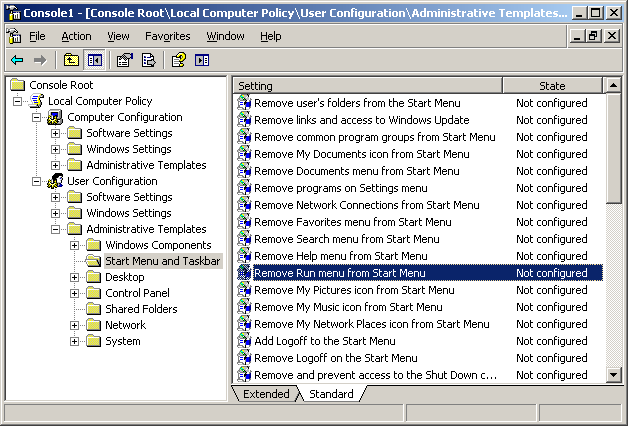
The properties window of the setting appears as shown in the below screenshot:
12. Click Enabled to enable this setting.
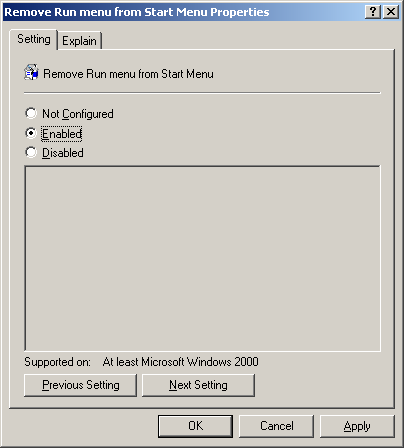
Once you click on 'OK', the local policy that you have applied will take effect and all the users who would log on to this computer will not be able to see the Run menu item of the Start menu.
This completes our Local Group Policy configuration section. Next section covers Domain Group Policies, that will help you configure and control user access throughout the Active Directory Domain.
Article Summary
Group Policies are an Administrator's best friend. Group Policies can control every aspect of a user's desktop, providing enhanced security measures and restricting access to specified resouces. Group policies can be applied to a local server, as shown on this article, or to a whole domain.
If you have found the article useful, we would really appreciate you sharing it with others by using the provided services on the top left corner of this article. Sharing our articles takes only a minute of your time and helps Firewall.cx reach more people through such services.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














