Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
|
Articles:
OpenMosix - Part 5: Testing Your Cluster
| Read |
| Read | |
|
Articles:
OpenMosix - Part 3: Using ClusterKnoppix
| Read |
| Read | |
| Read | |
Suggested Articles:
OpManager - Network Monitoring & Management
Network Management Systems Help Businesses Accura…
Accurately monitoring your organization’s business application performance, service provider SLA breaches, network infrastructure traffic, bandwidth…

ManageEngine Firewall Analyzer
Challenges & Solutions to Managing Firewall Rules…
In today's interconnected digital landscape, where businesses rely heavily on networked systems and the internet for their operations, the importance…

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into OpM…
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberattac…

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool: 7…
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectively…
Featured Subcategories:
WireShark Articles:
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
Detect Brute-Force Attacks with nChronos Network…
Brute-force attacks are commonly known attack methods by which hackers try to get access to restricted accounts and data using an exhaustive list/dat…
How to Use Multi-Segment Analysis to Troubleshoot…
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troublesho…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!

Palo Alto Networks
Configuring QoS on Palo Alto Firewalls: Class-based Po…
This article’s purpose is to help you quickly master Palo Alto QoS concepts and learn to configure QoS on Palo Alto Firewalls in a simple and efficient wa…
Palo Alto Networks
Palo Alto Firewall Application-based Policy Enforcemen…
Our previous article examined the benefits of Palo Alto Networks Firewall Single Pass Parallel Processing (SP3) architecture and how its combine with the…

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on P…
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a P…
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Windows Servers
Windows Server Group Policy Link Enforcement, Inherita…
Our previous article explained what Group Policy Objects (GPO) are and showed how group policies can be configured to help control computers and users wit…
Windows Servers
Introduction To Windows Server 2012 R2 Virtualization…
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer that…
Windows Servers
Windows Server 2016 VM Backup with Altaro's New VM Bac…
Altaro has released Altaro VM Backup, a faster and lighter upgrade to its flagship Hyper-V and VMware backup solution, which now supports all Windows Serv…
Windows Servers
Free Webinar: Troubleshooting & Fixing Microsoft Hyper…
Users working with Hyper-V Virtualization would be interested to know that Altaro is hosting a free webinar on the 25th of February 2016 at 4pm CET / 10am…
Popular Topics
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HTTP Us…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis applicati…

Virtualization & VM Backup
Ultimate Guide: Install Windows 11 on VMware ESXi – Ea…
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version 2.0 (…
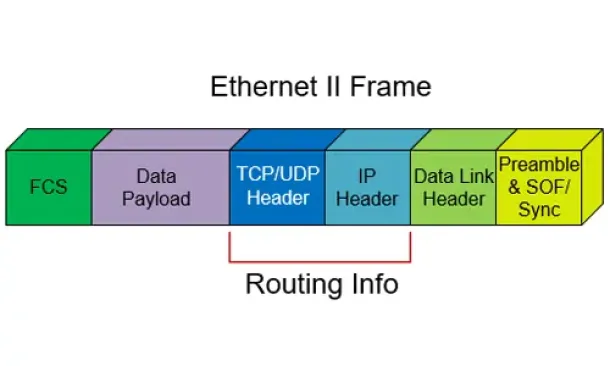
Routing
Routed Protocols
We all understand that TCP/IP, IPX-SPX are protocols which are used in a Local Area Network (LAN) so computers can communicate between with each other and…
Windows Servers
Installation and Configuration of Fine-Grained Passwor…
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server since the…
Cisco Services & Technologies
Cisco VPN Client & Windows 8 (32bit & 64bit) - Reason…
The Cisco VPN client is one of the most popular Cisco tools used by administrators, engineers and end-users to connect to their remote networks and access…
Cisco Services & Technologies
Renewing Cisco Certifications without sitting for a Ci…
Without a doubt, Cisco certifications and specializations are among the most popular vendor certifications in the IT industry, and earning them doesn’t co…
Cisco Routers
Configuring Cisco Site to Site IPSec VPN with Dynamic…
This article serves as an extension to our popular Cisco VPN topics covered here on Firewall.cx. While we’ve covered Site to Site IPSec VPN Tunnel Between…
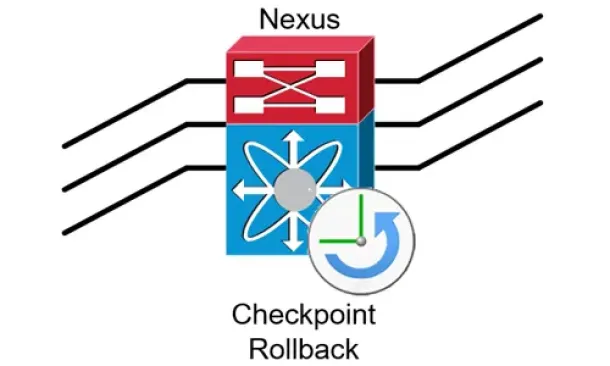
Cisco Data Center (Nexus/UCS)
Complete Guide to Nexus Checkpoint & Rollback Feature…
The Cisco NX-OS checkpoint feature provides the capability to capture at any time a snapshot (backup) of the Cisco Nexus configuration befo…



















