How to Test for SQL Injection Attacks & Vulnerabilities
 SQL injection vulnerabilities have held the first spot on the OWASP Top 10 list for quite some time. This is due to the fact that they are both still widespread and can lead to very serious consequences. Many major security breaches were caused by SQL injections, even in recent months. For example, this type of vulnerability caused a leak of financial data for more than 70 percent of citizens of Bulgaria.
SQL injection vulnerabilities have held the first spot on the OWASP Top 10 list for quite some time. This is due to the fact that they are both still widespread and can lead to very serious consequences. Many major security breaches were caused by SQL injections, even in recent months. For example, this type of vulnerability caused a leak of financial data for more than 70 percent of citizens of Bulgaria.
However, SQL vulnerabilities are also easy to discover automatically using web vulnerability scanners. Advanced web security scanning software can detect even the more advanced type of SQL injections such as blind SQL injections. SQL injections are also easy to fix and avoid. Developers can use parameterized queries (prepared statements) or stored procedures to avoid the root cause of SQL injections, which is the direct use of untrusted user input in SQL queries.
In this article, we will show you how to scan your web applications for SQL injections using the latest version of Acunetix. The scan will be performed on the VulnWeb site by Acunetix, which is intentionally vulnerable to attacks. The article assumes that you have downloaded and installed the Acunetix demo.
Key Topics:
Related Articles
- Everything You Need to Know About SQL Injection Attacks & Types, SQLi Code Example, Variations, Vulnerabilities & More
- What is Cross-site Scripting (XSS)? Why XSS is a Threat, how does XSS Work? Different Types of XSS Attacks
- Creating a Cross-site Scripting (XSS) Attack. Understanding How XSS Attacks Work & Identifying Web Vulnerabilities
STEP 1: CREATING A SCAN TARGET
To begin testing your web application for SQL injections, you need to add your web application URL as the target.
- Click on the Targets icon in the menu on the left. The Targets pane is displayed.
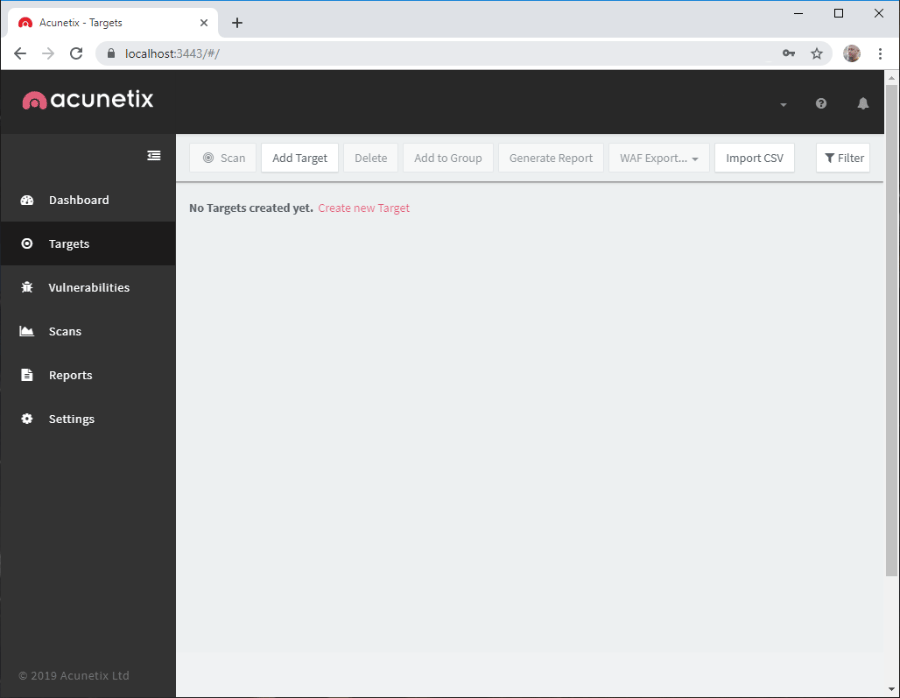
- Click on the Add Target button. The Add Target dialog is displayed. In the Address field, enter the full URL of your web application. Optionally, in the Description field, enter a human-readable description of your target:
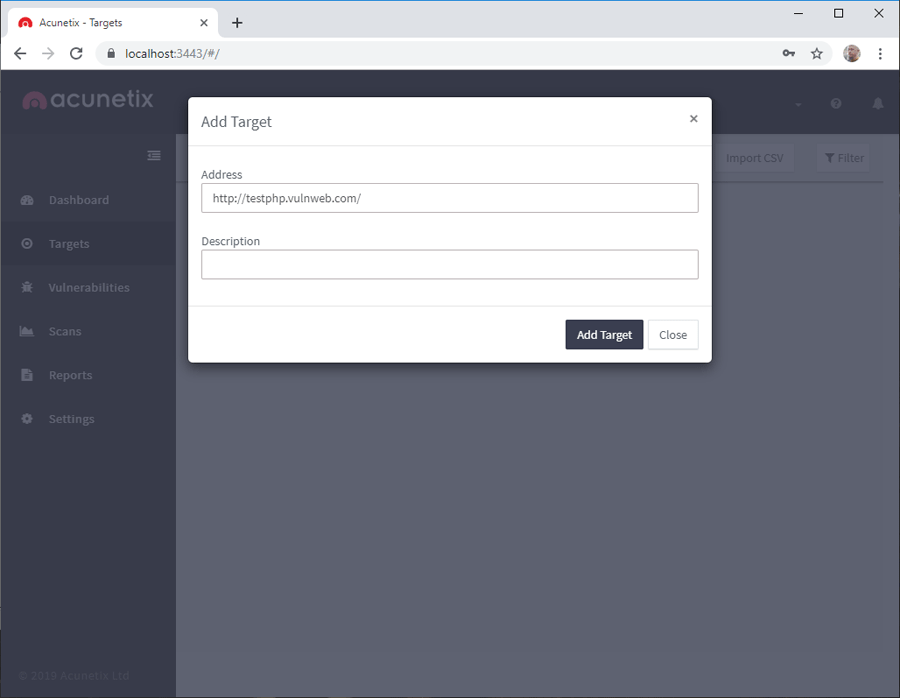
- Click on the Add Target button in the Add Target dialog. The Target Info pane is displayed:
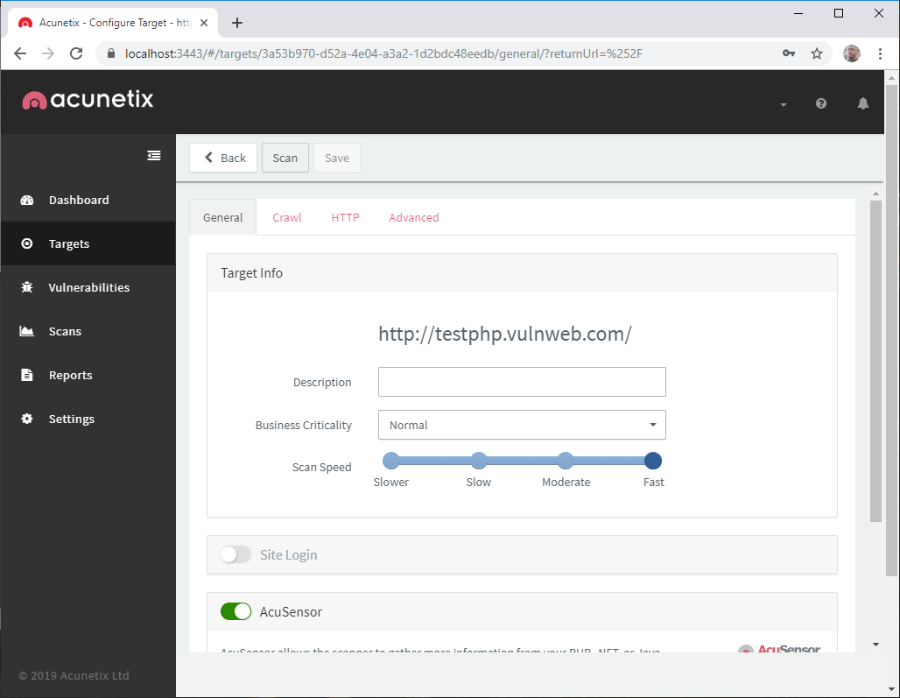
- In the Target Info pane, you can configure additional properties of the target. For example, you may choose to use AcuSensor technology, which requires that you install the AcuSensor agent on your web server. We recommend that you use this technology to increase the precision of your scanning.
STEP 2: PERFORMING A SCAN
Once your target is added and configured, you can scan it whenever you need to. You can also schedule your scans for the future. There are different types of scans, depending on your current needs. In this article, we will perform an SQL injection scan.
- Click on the Scan button in the Target Info pane. You can also click on the Scans icon in the left-hand menu to open the Scans pane, select the target by clicking on the leftmost column, and click on the New Scan button. The scan is started. You can see the progress of the scan in the Activity section:
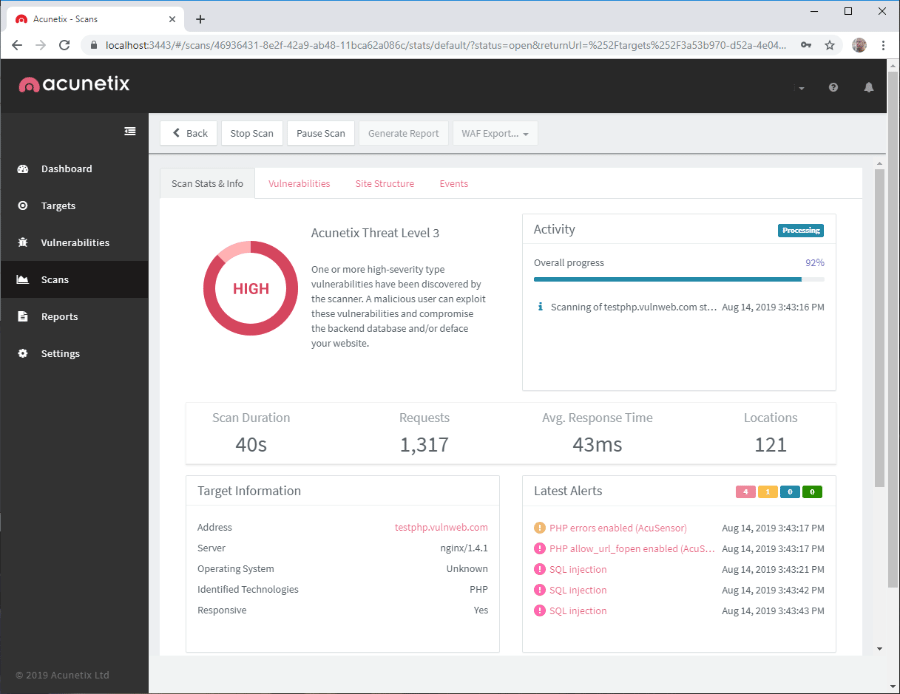
- When the scan is finished, a Completed icon will be visible in the Activity section:
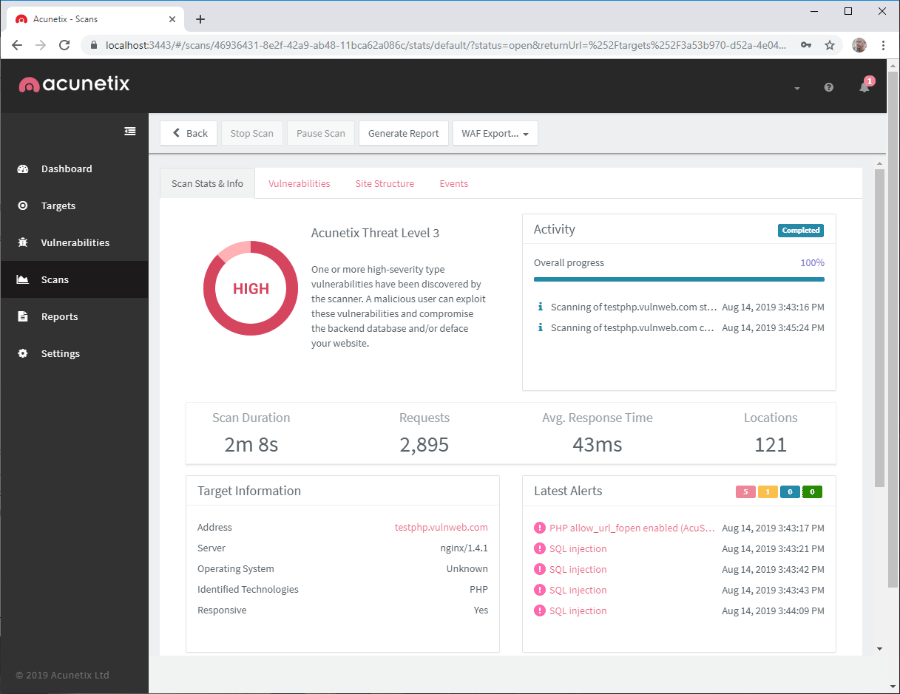
STEP 3: INTERPRETING RESULTS
When the scan is completed, you can analyze the details of the discovered vulnerabilities so that you know how to eliminate them. Acunetix provides additional information about all vulnerabilities as well as helpful links that teach you how to fix the issue.
- To see the details of vulnerabilities discovered during the scan, click on the Vulnerabilities tab. You can also click on the Vulnerabilities icon in the left-hand menu to see vulnerabilities for all targets at the same time:
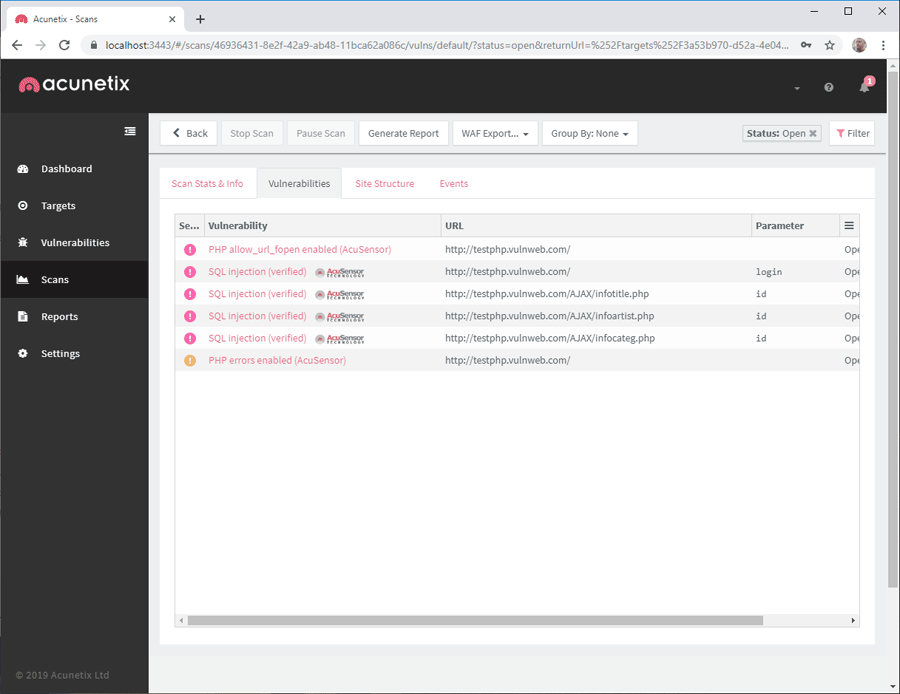
- To see the details of a selected vulnerability, click on the row in the table that represents the vulnerability. The vulnerability details panel is displayed:
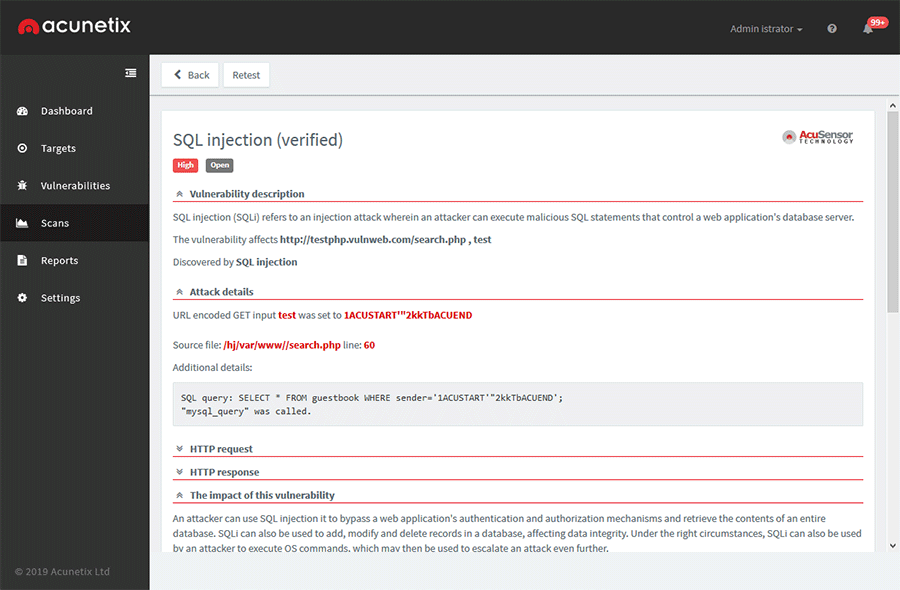
As you can see above, Acunetix provides exact details of the payload and the resulting SQL query. Since AcuSensor technology was used, the report also shows the source file and the line of code causing the SQL Injection vulnerability.
Summary
This article showed how to detect SQL Injection Vulnerabilities on your website, web application and CMS system. We saw how easy and quickly the Acunetix Web Vulnerability Scanner can be used to scan and obtain a full report of all SQL Injection vulnerabilities and exploits your systems are susceptible to.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














