Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
| Articles | |
|---|---|
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
| Read | |
MS Server Articles:
Windows Servers
Troubleshooting Windows Server 2012 R2 Crashes. A…
There are umpteen reasons why your Windows Server 2012 R2 decides to present you with a Blue Screen of Death (BSOD) or the stop screen. As virtual ma…
Windows Servers
Introduction To Windows Server 2012 R2 Virtualiza…
FREE Hyper-V & VMware Backup: FREE for Firewall.cx readers for a Limited Time! Download Now!
Virtualization is an abstraction layer…
Windows Servers
Hyper-V Best Practices - Replica, Cluster, Backup…
Hyper-V has proven to be a very cost effective solution for server consolidation. Evidence of this is also the fact that companies are beginning to m…
Windows Servers
How to Install/Enable Telnet Client for Windows S…
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this…
Featured Subcategories:
Virtualization & VM Backup Articles:

Ultimate Guide: Install Windows 11 on VMware ESXi…
In this article, we’ll show you how to setup or install Microsoft Windows 11 on VMware’s ESXi servers and bypass the Trusted Platform Module version…
How to Fix VMware ESXi Virtual Machine 'Invalid S…
In this article, we'll show you how to deal with VMs which are reported to have an Invalid Status as shown in the screenshot below. This is a co…
5 Most Critical Microsoft M365 Vulnerabilities Re…
Microsoft 365 is an incredibly powerful software suite for businesses, but it is becoming increasingly targeted by people trying to steal your data…
Differences Between VMware vSphere, vCenter, ESXi…
In this article we will cover the differences between VMware ESXi, vSphere and vCenter while also explain the features supported by each vSphere edit…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Linux - Unix
Why Use Linux?
The first question is - what are the benefits of using Linux instead of Windows? This is in fact a constant debate between the Windows and Linux communiti…
Linux - Unix
Understanding, Administering Linux Groups and User Acc…
In a multi-user environment like Linux, every file is owned by a user and a group. There can be others as well who may be allowed to work with the file. W…
Linux - Unix
Linux BIND DNS - Part 4: Common BIND Files - Named.loc…
So far we have covered in great detail the main files required for the firewall.cx domain. These files, which we named db.firewall.cx and db.192.168.0, de…
Linux - Unix
Installing Software On Linux
Installing software in Linux is very different from Windows for one very simple reason: most Linux programs come in 'source code' form. This allows you to…
Popular Topics
OpManager - Network Monitoring & Management
Free Webinar: Learn How Zero-Trust & Cloud Technologie…
Work transformation is not 'one and done,'" says IDC's vice president, Holly Muscolino. Most enterprises understand that a hybrid workforce is the f…
Cisco Switches
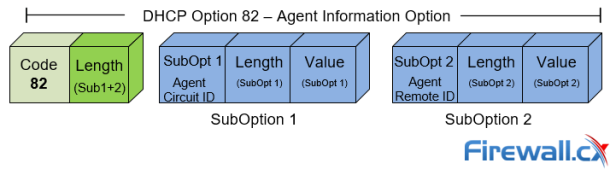
DHCP Option 82 Message Format, Analysis. DHCP Snooping…
This article provides in-depth analysis of DHCP Option 82 (DHCP Relay Agent) which is one of the +180 DHCP Options available to the DHCP protocol and used…

VLAN Networks
VLAN Security - Making the Most of VLANs
It's easy to see why virtual LANs have become extremely popular on networks of all sizes. In practical terms, multiple VLANs are pretty much the same as h…
Windows Workstations (XP, 7, 8, 10, 11)
Configuring Windows 7 To Provide Secure Wireless Acces…
Not many people are aware that Windows 7 has built-in capabilities that allow it to be transformed into a perfectly working access point so that wireless…


















