SASE and VPNs: Reconsidering your Mobile Remote Access and Site-to-Site VPN strategy
 The Virtual Private Network (VPN) has become the go to security solution for keeping communications between networks and endpoints secure. After all, VPNs offer a straightforward, secure method for connecting sites (a site-to-site VPN) that couldn’t justify a high-end, MPLS service, and they enable mobile users to get secure connectivity from anywhere (mobile VPN). Deployment is quick, availability is high, only requiring Internet access, and network costs relatively low given the use of affordable Internet capacity.
The Virtual Private Network (VPN) has become the go to security solution for keeping communications between networks and endpoints secure. After all, VPNs offer a straightforward, secure method for connecting sites (a site-to-site VPN) that couldn’t justify a high-end, MPLS service, and they enable mobile users to get secure connectivity from anywhere (mobile VPN). Deployment is quick, availability is high, only requiring Internet access, and network costs relatively low given the use of affordable Internet capacity.
Yet, for all that praise, VPNs are far from perfect. They require IT to purchase and deploy separate VPN appliances, increasing capital costs and complicating maintenance. Most VPN solutions require frequent patching, user policy settings, reconfiguration, and oversite. All of which adds to the burden of attempting to maintain security. What’s more, VPNs can introduce latency into mobile connections, as well as require additional login steps, often confusing end users and adding to the burden of the help desk.
All of which issues beg the question: Is it time to drop your VPN and find a better solution for site-to-site and mobile access?
Before we answer the question, let’s take a look at the key topics covered here:
- SASE or VPN: What’s the Difference?
- SASE Brings VPN Benefits without VPN’s Networking Weaknesses
- SASE Makes Security Much Easier
- SASE Answers the VPN Questions
Until recently, the answer to our question above would have been “no.” There wasn’t a better answer out there. However, as networking technology has evolved, an answer to the VPN conundrum may be found in Secure Access Service Edge (SASE), the successor to SD-WAN and, quite possibly, VPNs. Here’s why.
SASE or VPN: What’s the Difference?
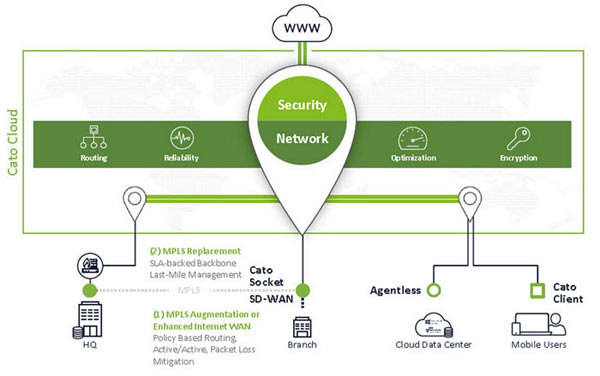
SASE originates from a proposal by research giant Gartner, which defined SASE as a cloud architecture model combining the functions of different network and security solutions into a unified, cloud security platform.
SASE, as envisioned by Gartner, operates as a cloud-naive service connecting all of an organization’s “edges” – including sites, mobile users, IoT devices, and cloud resources -- into a single, global secure network. It’s cloud-native meaning that the software has all of the scalability, elasticity, and repaid deployment benefits of the cloud.
And the network is secure. We don’t just mean secure as an encrypted network, like SD-WAN. We mean one that also has a complete, embedded security stack protecting against Internet-borne threats. More specifically Next-Generation Firewall (NGFW), CASB, SWG, ZTNA, RBI, and DNS are all part of the SASE platform.
Devices of different sorts establish encrypted tunnels to the SASE point of presence (PoP). The software in the SASE PoP authenticates connecting user and grants access to defined resources based on user identity and real-time conditions, such as the user’s location or device.
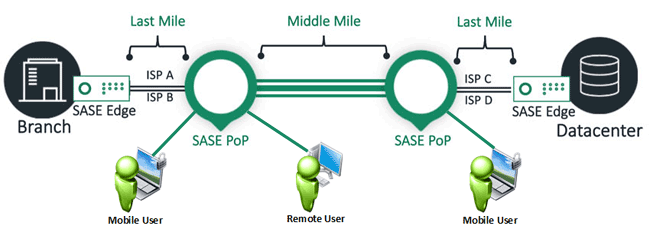
Incoming traffic is inspected in a single-pass with SASE applying the complete range of security functions, optimized, and forwarded along the optimum path to its destination. As such, edges gain the best possible network experience anywhere in the world, at least that’s the theory.
SASE Brings VPN Benefits without VPN’s Networking Weaknesses
Like a VPN, SASE can operate securely over the Internet making it affordable and available everywhere. But SASE goes a few steps further than any contemporary VPN solution, bringing the kinds of performance and ease of use that previously were only afforded to sites. In short, SASE makes sites, mobile users, IoT devices and cloud resources “equal citizens” of the new WAN.
SASE simplifies deployment and maintenance by eliminating additional, specialized VPN hardware and concentrators. Instead, sites and mobile users connect directly to the SASE PoP. Sites via SASE’s global SD-WAN service; mobile users connect via client or clientless access.
And by establishing tunnels to the nearest PoP and not to one another, SASE avoids the deployment and recovery problems of full mesh, site-to-site VPNs. In those networks, where sites maintain direct tunnels with every other location in the network, significant time is spent first by IT personnel configuring the tunnels and then by the VPN device re-establishing tunnels after a network failure. With SASE, sites only establish one or two tunnels to the local PoP. This is done automatically, making initial deployment very easy, and with so few tunnels, recovering from a network failure can be in a fraction of the time even for what was a very large, meshed network.
SASE also addresses the performance problem faced by VPNs. The WAN optimization and route optimization built into SASE improves traffic performance for all edges. With VPNs, those technologies either weren’t possible (in the case of mobile users) or would have required additional investment (in the case of site-to-site VPNs).
What’s more by SASE eliminates the backhaul that undermines mobile VPN performance. Instead of bring Internet and cloud traffic back to a central inspection point, as is the case with VPNs, SASE brings security inspection to the local PoP. Traffic hits the nearest PoP, gets inspected, and is forwarded directly onto its destination.
SASE Makes Security Much Easier
Not only does SASE address VPN’s networking limitations but having a single security engine for traffic from any edge significantly simplifies security policy management and enforcement.
Access control is much tighter. Rather than giving remote users access to the entire networks, SASE uses cloud-based Software Defined Perimeter (SDP) or zero trust network access (ZTNA), which restricts network access to authorized resources. Users only see the network resources, be they applications or hosts, permitted by their policy. There’s no opportunity for them to “PING” or use other IP tools to investigate the network and uncover unprotected resources. SDP uses strong authentication on access and continuous traffic inspection, helping to further secure endpoints.
Security management is also much easier particularly when combining VPNs with SD-WANs. Rather than maintaining separate security policies for the mobile users connected by VPN and office users sitting behind the SD-WAN device, SASE creates a single set of security policies for all users and resources.
SASE Answers the VPN Questions
SASE with cloud-based SDP proves to be faster, more secure, and easier to manage than legacy VPN systems. It’s the obvious choice for those looking for a modern VPN or to benefit from the combination of VPNs and SD-WAN.
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














