Articles
To read the articles in this section, simply click on the article title or read button on the far right (if visible).
Use the below filters to customise the number of articles displayed or search for specific title topics/keywords.
Suggested Articles:
Network Protocol Analyzers
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Network Protocol Analyzers
How to Reconstruct HTTP Packets/Data & Monitor HT…
HTTP reconstruction is an advanced network security feature offered by nChronos version 4.3.0 and later. nChronos is a Network Forensic Analysis appl…

OpManager - Network Monitoring & Management
Maximizing Network Security: A Deep Dive into OpM…
In the rapidly evolving landscape of cyber threats, network security has never been more crucial. With the frequency and sophistication of cyberattac…
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops wi…
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by u…
Featured Subcategories:
WireShark Articles:
How to Detect P2P (peer-to-peer) File Sharing, To…
Peer-to-Peer file sharing traffic has become a very large problem for many organizations as users engage in illegal (most times) file sharing process…
Introducing Colasoft Unified Performance Manageme…
Colasoft Unified Performance Management (UPM) is a business-oriented network performance management system, which analyzes network performance, quali…
Advanced Network Protocol Analyzer Review: Colaso…
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last review…
How to Detect SYN Flood Attacks with Capsa Networ…
This article explains how to detect a SYN Flood Attack using an advanced protocol analyser like Colasoft Capsa. We’ll show you how to identify and in…
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Palo Alto Networks Firewall - Web & CLI Initial Config…
This article is the second-part of our Palo Alto Networks Firewall technical articles. Our previous article was introduction to Palo Alto Networks Firewal…
Palo Alto Networks
How to Fix Palo Alto Firewall “Error: Image File Authe…
Keeping your Palo Alto Firewall up to date with the latest PAN-OS software updates is an important step to ensure your organization is protected against t…
Palo Alto Networks
Complete Guide to Upgrading Palo Alto Firewall PAN-OS…
Upgrading your Palo Alto Firewall or Panorama Management System to the preferred PAN-OS release is always recommended as it ensures it remains stable, saf…
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, Vi…
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain the…
Windows Servers
How to Install Windows 2012 Hyper-V via Server Manager…
Our previous article covered the basic concepts of Virtualization and Windows Server 2012 Hyper-V. This article takes a closer look at Microsoft’s H…
Windows Servers
Free Webinar & eBook on Microsoft Licensing for Virtua…
Microsoft Licensing for Virtual environments can become a very complicated topic, especially with all the misconceptions and false information out there…
Windows Servers
New Features in Windows Server 2012 - Why Upgrade to…
There is no doubt that Cloud Computing is hot topic these days. Innovations in cloud computing models have made every industry and company IT departments…
Windows Servers
Download Altaro Free VM Backup & Win a PlayStation 4 P…
We have some exciting news for you today!
Altaro has launched a great contest in celebration of SysAdmin Day on 27th July!
They will be giving away Amaz…
Popular Topics
Virtualization & VM Backup
How to Enable SNMP on VMware ESXi Host & Configure ESX…
In this article we will show you how to enable SNMP on your VMware ESXi host, configure SNMP Community string and configure your ESXi firewall to allow or…
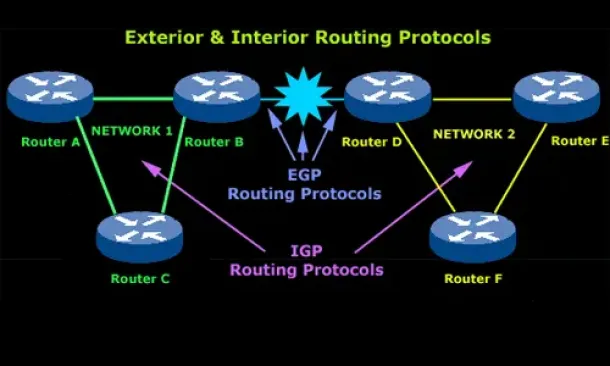
Routing
Introduction to Routing Protocols
Distance Vector, Link State RIP, IGRP, EIGRP, OSPF
Routing protocols were created for routers. These protocols have been designed to allow the exchange…
Virtualization & VM Backup
6 Key Areas to Consider When Selecting a VM Backup Sol…
Backup and Disaster recovery are core considerations for any business with an IT footprint, whether that is on-premises or in the cloud.
Your business de…
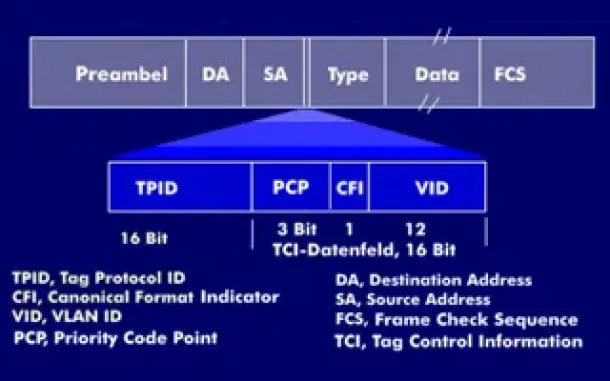
VLAN Networks
VLAN Tagging - Understanding VLANs Ethernet Frames
We mentioned that Trunk Links are designed to pass frames (packets) from all VLANs, allowing us to connect multiple switches together and independently co…
Cisco Routers
How To Configure DHCP Server On A Cisco Router
DHCP (Dynamic Host Configuration Protocol) is the protocol used by network devices (such as PCs, network printers, etc) to automatically obtain correct ne…
Cisco Switches
Cisco Nexus 7000 Series Module Shutdown and Removal Pr…
This article explains the procedure that should be followed to correctly shutdown/powerdown a Cisco Nexus 7000 series module and remove it from the chassi…
Cisco Routers
Configuring Cisco Site to Site IPSec VPN with Dynamic…
This article serves as an extension to our popular Cisco VPN topics covered here on Firewall.cx. While we’ve covered Site to Site IPSec VPN Tunnel Between…
Cisco CallManager-CCME
Introduction to Cisco Unified Communication Manager Ex…
We have been hearing about VoIP for many years now and while some have never worked with it, it has become today's standard in IP Communications and Priva…



















