Cisco Router 'Privileged' Mode
To get into Privileged Mode we enter the "Enable" command from User Exec Mode. If set, the router will prompt you for a password. Once in Privileged Mode, you will notice the prompt changes from ">" to a "#" to indicate that we are now in Privileged Mode.
The Privileged Mode (Global Configuration Mode) is used mainly to configure the router, enable interfaces, setup security, define dialup interfaces etc.
We've included a screenshot of the router to give an idea of the commands available in Privileged Mode in comparison to the User Exec Mode. Remember that these commands have sub-commands and can get quite complicated:
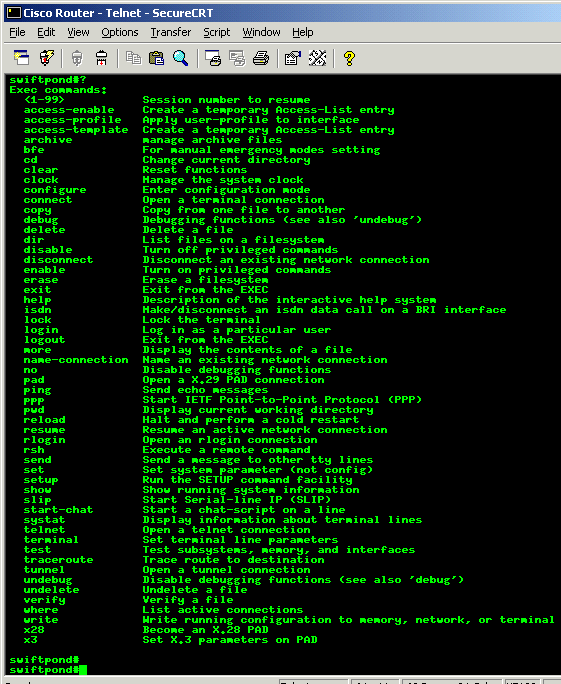
As you can see, there is a wider choice of commands in Privileged Mode.
Now, when you want to configure certain services or parts of the router you will need to enter Global Configuration Mode from within Privileged Mode. If you're confused by now with the different modes available try to see it this way:
User Exec Mode (distinguished by the ">" prompt) is your first mode, which is used to get statistics from router, see which version IOS you're running, check memory resources and a few more things.
Privileged Mode (distingushed by the "#" prompt) is the second mode. Here you can enable or disable interfaces on the router, get more detailed information on the router, for example, view the running configuration of the router, copy the configuration, load a new configuration to the router, backup or delete the configuration, backup or delete the IOS and a lot more.
Global Configuration Mode (distingushed by the (config)# prompt) is accessable via Privileged Mode. In this mode you're able to configure each interface individually, setup banners and passwords, enable secrets (encrypted passwords), enable and configure routing protocols and a lot more. We dare say that almost everytime you want to configure or change something on the router, you will need to be in this mode.
Entering Global Configuration
The picture below shows you how to enter Global Configuration Mode:
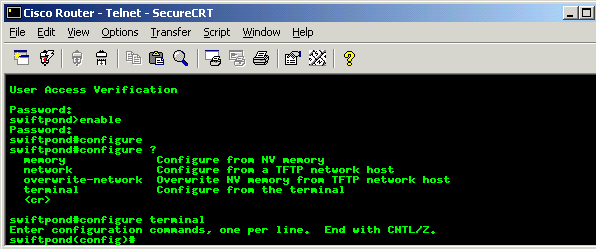
As you can see, we have telneted into the router and it prompted for a password. We entered the password, which is not shown, at this point we are in User Exec Mode and then entered "enable" in order to get into the Privileged Mode. From here to get into Global Configuration Mode you need to enter the "configure selection" command.
Now you must be wondering what the various parameters shown in the picture are, under the "configure" command. These allow you to select how you will configure the router:
- Configure Memory means you enter Global Configuration Mode and are configuring the router in its NVRAM. This command will force the router to load up the startup-config file stored in the NVRAM and then you can proceed with the configuration. When you're happy with the configuration, save it to NVRAM by entering "copy running-config startup-config".
- Configure Network means you enter Global Configuration Mode and load a startup-config file from a remote router (using tftp) into your local router's memory and configure it. Once you're finished, you need to enter "copy running-config tftp" which will force the router to copy its memory configuration onto a tftp server. The router will prompt you for the IP address of the remote tftp server.
- Configure Overwrite-network means that you overwrite the NVRAM's configuration with a configuration stored on a tftp server. Issuing this command will force the router to prompt for an IP address of the remote tftp server. This command is rarely used.
- Configure Terminal means you enter Global Configuration Mode and work with the configuration which is already loaded into the router's memory (Cisco calls this the running-config). This is the most popular command, as in most cases you need to modify or re-configure the router on the spot and then save your changes.
You will need to save this configuration otherwise everything you configure will be lost upon power failure or reboot of the router!
Below are the commands you need to enter to save the configuration, depending on your network setup:
- Copy running-config startup-config: Copies the configuration which is running in the router's RAM in to the NVRAM and gives it a file name of startup-config (default). If one already exists in the NVRAM, it will be overwritten by the new one.
- Copy running-config tftp: Copies the configuration which is running in the router's RAM in to a tftp server which might be running on your network. You will be asked for the IP address of the tftp server and given the choice to select a filename for the configuration. Some advanced routers can also act as tftp servers.
Generic Configuration
There are a few standard things with which you always need to configure the router . For example, a hostname. This is also used as a login name for the remote router to which your router needs to authenticate. Before we get stuck into the interface configuration we are going to run through a few of these commands. The following examples assume no passwords have been set as yet and that the router has a default hostname of "router":
We connect to the router via the console port using the serial cable and type the following:
This is a standard way of authentication with Cisco routers. Your router's hostname is your login name and your password (in our case "firewallcx") is entered at the same time you define the remote router's hostname.
Next we create a static route so the router will pass all packets originating from our network to the remote router. This is usually the case when you connect to your isp.
With the above command we tell our router to create a default route where any packet -defined by the first 0.0.0.0- no matter what subnetmask -defined by the second 0.0.0.0- is to be sent to ip 139.130.34.43 which would be the router we are connecting to.
In the case where you were not configuring the router to connect to the Internet but to join a small WAN which connects a few offices, then you probably want to use a routing protocol:
Alternatively, you can use IGRP as a routing protocol, in which case you would have to enter the following:
After that, we need to create a dialer list which our WAN interface BRI (ISDN) will use to make a call to our ISP.
We'll give you a quick example to make sure you understand the reason we put this command:
If you launched your web browser, it would send an http request to the server you have set as a homepage e.g www.firewall.cx. This request which your computer is going to send, is encapsulated in an ip packet that will cause your router to initiate a connection, as it is now configured to do so.
The dialup interface for Cisco routers is broken into 2 parts: a Dialer-list and a Dialer-group.
The Dialer-list defines the rules for placing a call. Later on when you configure the WAN interface, you bind that Dialer-list to the interface by using the Dialer-group command (shown later on).
Configuring Interfaces
In our example we said we have a router with one Ethernet and one basic ISDN interface (max of 128Kbit). We are going to go through the process of configuring the interfaces. We will start with the Ethernet Interface.
In order to configure the interface, we need to be in Global Configuration Mode, so we need to type first "enable" in order to get into Privileged Mode and then "configure terminal" to get into the appropriate Global Configuration Mode (as explained above). Now we need to select the interface we want to configure, in this case the first ethernet interface (E0) so we type "interface e0".
This picture shows clearly all the steps:
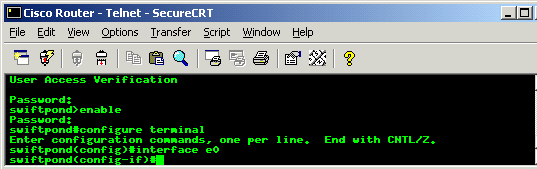
Any commands entered here will affect the first ethernet interface only. So we start with the IP address. It's important to understand that this IP address would be visible to both networks to which the router is connected. If we were connecting to the Internet then everyone would be able to see this IP. Futhermore, the IP address would also be the default gateway for our firewall or machine which would physically connect directly to the router.
The following commands will configure the ethernet interface's IP address:
or
Now that we have given e0 its IP address, we need to give the ISDN interface its IP as well, so we need to move to the correct interface by typing the following:
Now when it comes to configuring WAN interfaces, you need more than just an IP address (LAN interfaces such as E0 are a lot easier to configure). You need to set the encapsulation type, the authentication protocol the router will use to authenticate to the remote router, the phone number it will need to dial and a few more:
That pretty much does it for our ISDN (WAN) interface. All you need to do now is to SAVE the configuration!
We hope it wasn't too bad for you, since there is a quite a bit of information on this page. We encourage you to read through it again until you understand what is going on, then you will find it a breeze to configure a Cisco router yourself!
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!














