Suggested Articles:
Network Protocol Analyzers
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...

ManageEngine Firewall Analyzer
Discover the Ultimate Firewall Management Tool:...
Firewall security management is a combination of monitoring, configuring, and managing your firewall to make sure it runs at its best to effectivel...
Network Protocol Analyzers
How to Detect Routing Loops and Physical Loops ...
When working with medium to large scale networks, IT departments are often faced dealing with network loops and broadcast storms that are caused by...
Network Protocol Analyzers
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...
Featured Subcategories:
WireShark Articles:
Advanced Network Protocol Analyzer Review: Cola...
Firewall.cx has covered Colasoft Capsa several times in the past, but its constant improvements make it well worth revisiting. Since the last revie...
How To Detect ARP Attacks & ARP Flooding With C...
ARP attacks and ARP flooding are common problems small and large networks are faced with. ARP attacks target specific hosts by using their MAC addr...
How to Perform TCP SYN Flood DoS Attack & Detec...
This article will help you understand TCP SYN Flood Attacks, show how to perform a SYN Flood Attack (DoS attack) using Kali Linux & hping3 and ...
How to Use Multi-Segment Analysis to Troublesho...
Troubleshooting network problems can be a very intensive and challenging process. Intermittent network problems are even more difficult to troubles...
Your IP address:
13.59.136.170
Wi-Fi Key Generator
Follow Firewall.cx
Cisco Password Crack
Decrypt Cisco Type-7 Passwords on the fly!
Palo Alto Networks
Introduction to Palo Alto Next-Generation Network Fi...
During the past decade, we’ve seen the global IT security market flooded with new network security and firewall security appliances. New vendors emergin...

Palo Alto Networks
Complete Guide: Configuring IPSec VPN between Palo A...
This article will show you how to configure an IPSec VPN tunnel between a Palo Alto firewall (all PANOS versions) and Meraki MX security appliance. Our ...
Palo Alto Networks
Palo Alto Firewall Configuration Options. Tap Mode, ...
Our previous article explained how Palo Alto Firewalls make use of Security Zones to process and enforce security policies. This article will explain th...

Palo Alto Networks
How to Manually Download, Import & Install PAN-OS on...
This article provides comprehensive guidance on the manual processes involved in downloading, uploading, and installing (import) any PAN-OS version on a...
Windows Servers
How to Install/Enable Telnet Client for Windows Serv...
IT professionals frequently need connectivity and management tools. The Telnet Client is one of the most basic tools for such activities. Using this too...
Windows Servers
How to Enable & Configure Shadow Copy for Shared Fol...
When you shadow copy a disk volume, you are actually generating a snapshot of the changes made to the folders and files within the disk volume at a cert...
Windows Servers
Installation and Configuration of Fine-Grained Passw...
Microsoft introduced Fine-Grained Password Policy for the first time in Windows Server 2008 and the policy has been part of every Windows Server since t...
Windows Servers
How to Easily Change Network Card Profile / Network ...
Network Location Awareness (NLA) is a feature offered on Windows Server 2012 R2 and all Windows workstation editions from Windows 8.1 and above, includi...
Popular Topics

VLAN Networks
VTP Introduction & Modes
The invention of VLANs was very much welcomed by all engineers and administrators, allowing them to extend, redesign and segment their existing network ...
Security Service Edge (SSE)
Security Service Edge (SSE) Limitations & Disadvanta...
This article explores the Security Service Edge (SSE) portion of Secure Access Service Edge (SASE) and the need for holistic cybersecurity protections.
...
Network Fundamentals
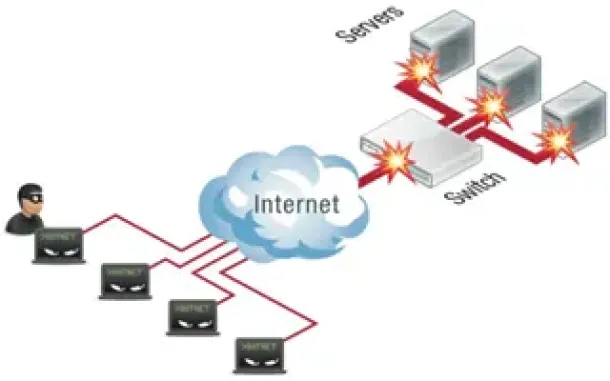
DoS & DDoS Attacks
A Denial of Service (DoS) attack is a malicious attempt to disrupt the normal functioning of a website, server or network by flooding it with traffic or...
Routing
Enhanced Interior Gateway Routing Protocol - EIGRP
Enhanced Interior Gateway Routing Protocol (EIGRP), similar to IGRP, is a Cisco proprietary routing protocol that is used to exchange routing informatio...
Cisco Services & Technologies
Introduction to Cisco VIRL – Virtual Internet Routin...
One of the most difficult things for people who are starting out in a networking career is getting their hands on the equipment. Whether you are studyin...
Cisco CallManager-CCME
How to Register Cisco IP Phones & Connect CallManage...
This article shows how to connect Cisco's Unified CallManager with a CallManager Express system (including UC520, UC540 and UC560) via H323 gateway, all...
Cisco Services & Technologies
Unified Communications Components - Understanding Yo...
What Is Unified Communications (UC)?
Unified communications is a very popular term these days and we see it appearing on almost every vendor as t...
Cisco Routers
Resolving Cisco Router/Switch Tftp Problems: Source ...
When working with Cisco equipment that has multiple ip interfaces, a common problem engineers are faced with is trying to successfully tftp to or from t...



















